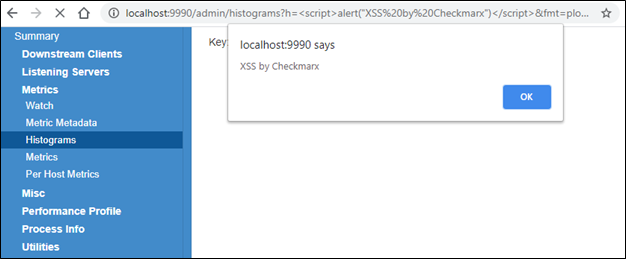
window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Descrição
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
GitHub - inforkgodara/xss-vulnerability: Explanation of Cross-site Scripting (XSS) with PHP mini project.

Add support for inline JS/CSS with #attached [#2391025]

Wacky XSS challenge write-up. On November 4th BugPoc published a new…, by Daniel Santos
writeups/bug.md at main · tess-ss/writeups · GitHub

eclipse - The type org.openqa.selenium.chrome.ChromeDriver is not accessible - Stack Overflow
GitHub Desktop unable to fetch (url has no scheme) · Issue #9597 · desktop/desktop · GitHub

Wacky XSS challenge write-up. On November 4th BugPoc published a new…, by Daniel Santos

Ckan, PDF, File Format

Penetration testing & window.opener — XSS vectors part 1, by Josh Graham, TSS - Trusted Security Services

Blind XSS To SSRF. During bug hunting in a private bug…, by Akash c
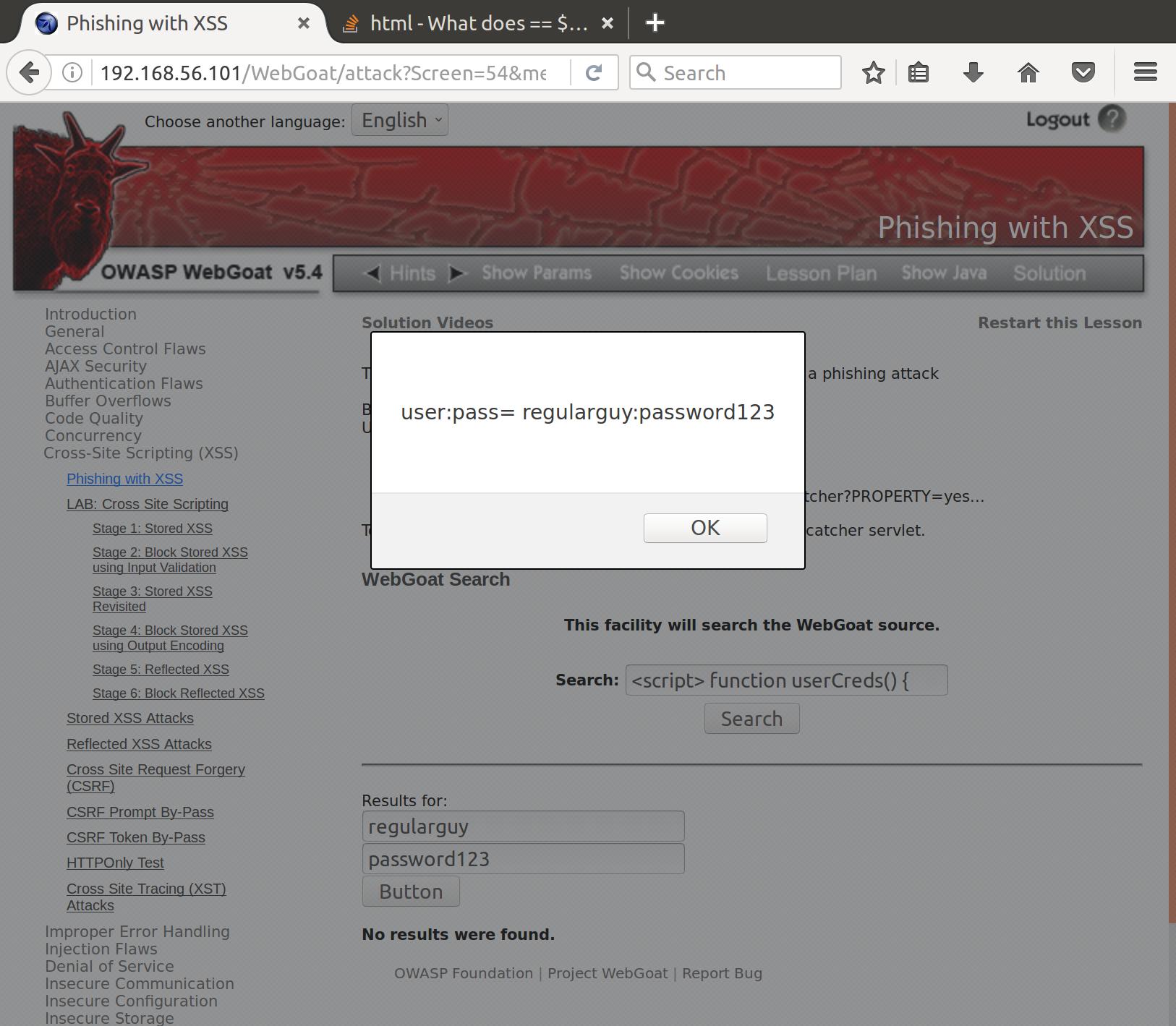
OWASP BWA WebGoat Challenge: Cross Site Scripting - byte-sized
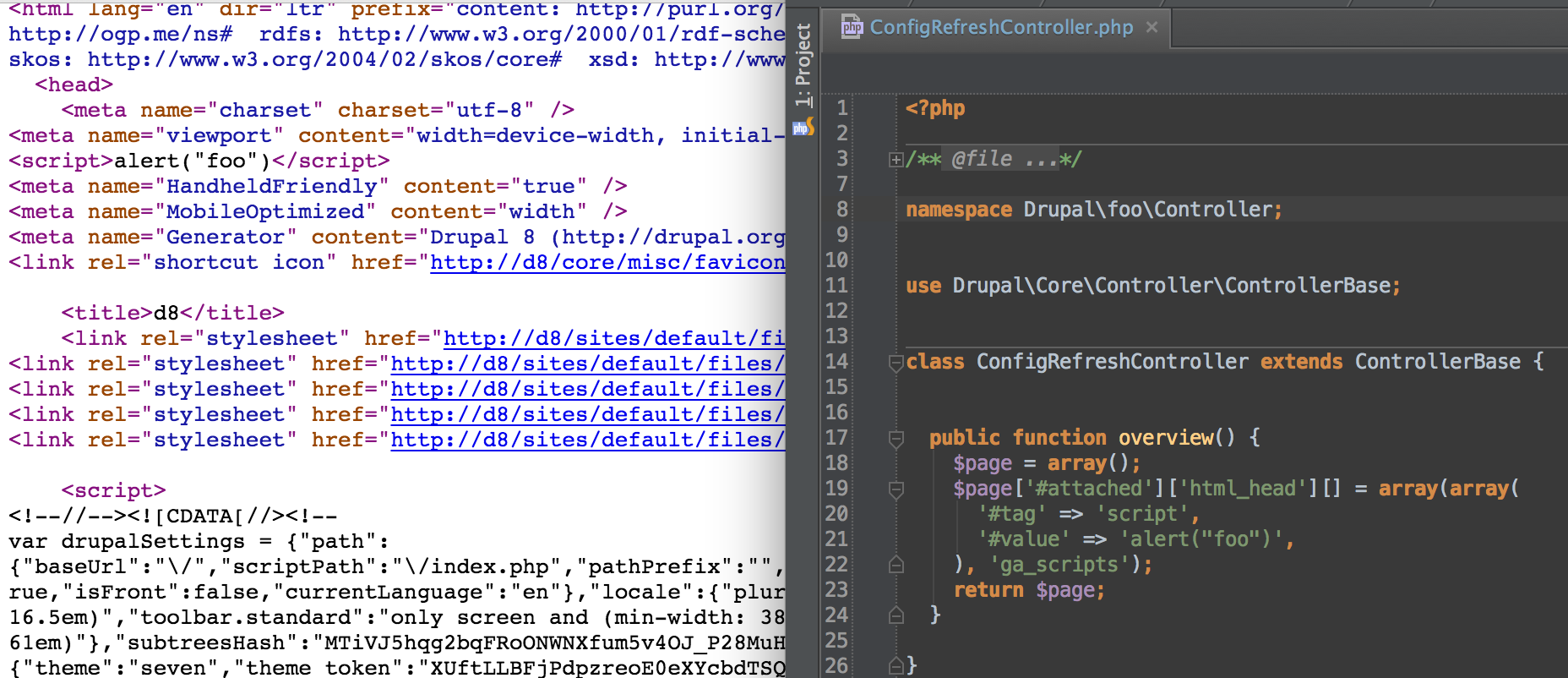
Add support for inline JS/CSS with #attached [#2391025]
XSS via File Upload, Lucideus Research, by Lucideus
de
por adulto (o preço varia de acordo com o tamanho do grupo)