Cryptojacking - Cryptomining in the browser — ENISA
Descrição
The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

PacNOG 23: Introduction to Crypto Jacking

What You Must Know About Cryptojacking in 2022

WP2018 O.1.2.1 - ENISA Threat Landscape 2018 PDF, PDF
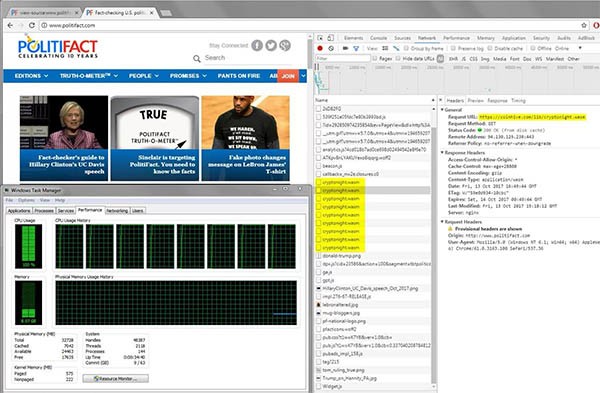
How Hackers Use Cryptojacking Malware to Take Over Computers to
My device is being used for cryptojacking

What is Cryptojacking. Criminals are now using ransomware-like
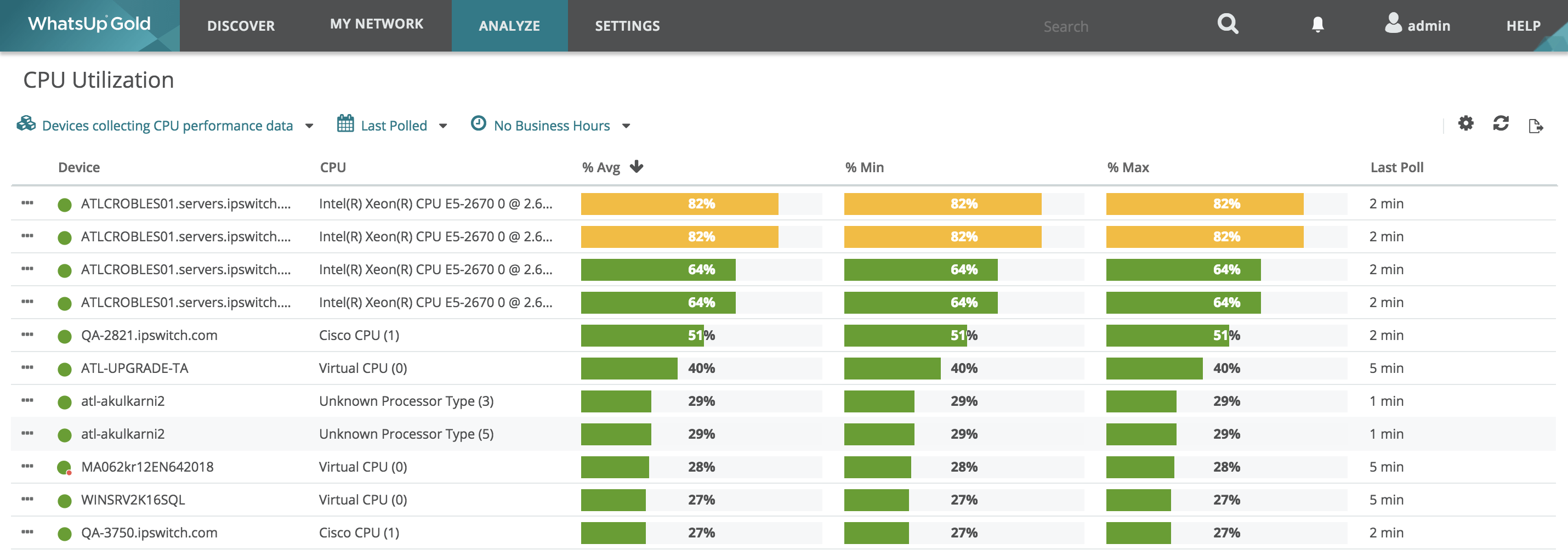
How to Detect and Stop Cryptomining on Your Network
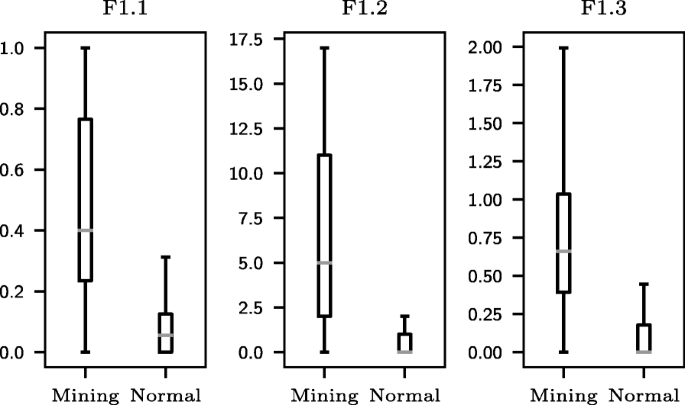
Detection of illicit cryptomining using network metadata

cisco Archives - STL Partners
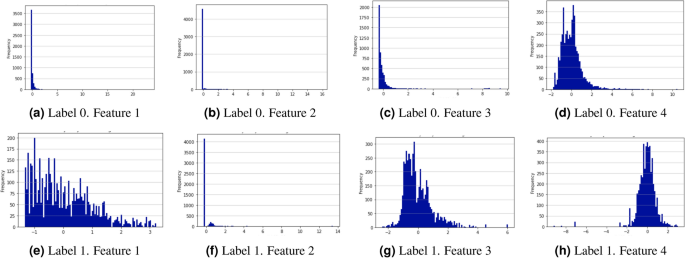
Synthetic flow-based cryptomining attack generation through

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs
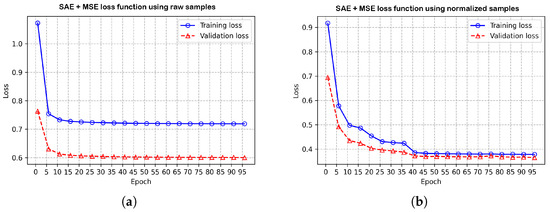
Applied Sciences, Free Full-Text

Cryptojacking
de
por adulto (o preço varia de acordo com o tamanho do grupo)