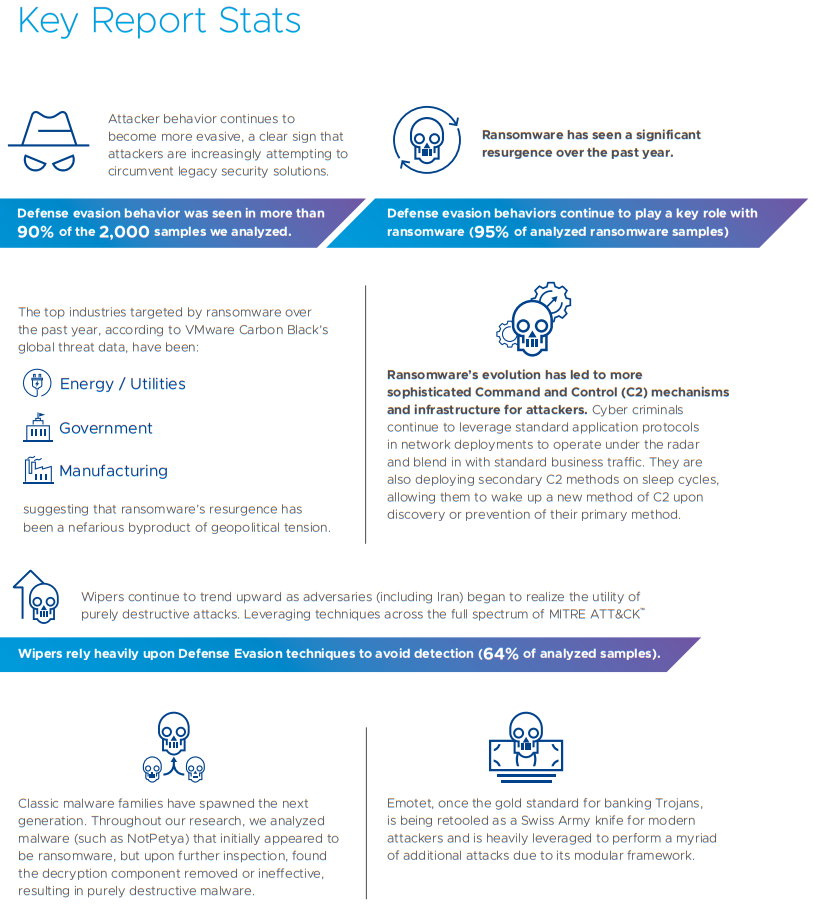
How ransomware attackers evade your organization's security
Descrição
How ransomware operators avoid your security solutions and what you can do to protect your network against post-compromise ransomware attacks.

10 Examples of Recent and Impactful Ransomware Attacks

Ransomware: Avoid Becoming the Next Victim, 2020-03-18

Why detection and response technology won't solve all ransomware attacks

9 stages of ransomware: How AI responds at every stage

Examples of Ransomware: 7 Cyber Security Trends To Fight Back

Top 7 Ransomware Attack Vectors & How to Avoid Becoming a Victim

Ransomware in Public Clouds: How TTPs Could Change

7 Steps to Help Prevent & Limit the Impact of Ransomware

15 ways to protect your company from Ransomware attacks - Red Level
Protect Against Potential Ransomware Attacks on Object Storage

RH-ISAC, Preventing Ransomware Attacks in a Hybrid Cloud
de
por adulto (o preço varia de acordo com o tamanho do grupo)
_new-roblox-evade-script-hack-gui-124-auto-farm-124-god-mode-124-infinite-money-amp-more-pastebin-2022-preview-hqdefault.jpg)