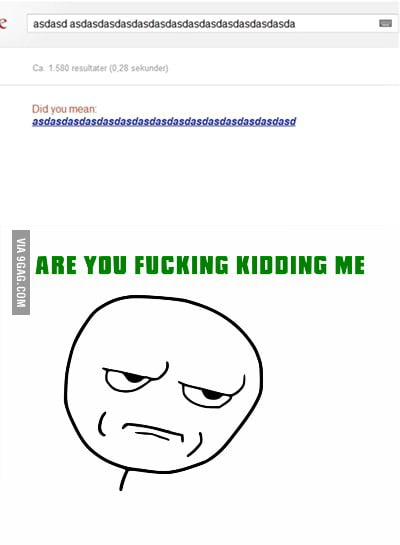
LetsDefend on X: Top 100 Reused Passwords / X
Descrição
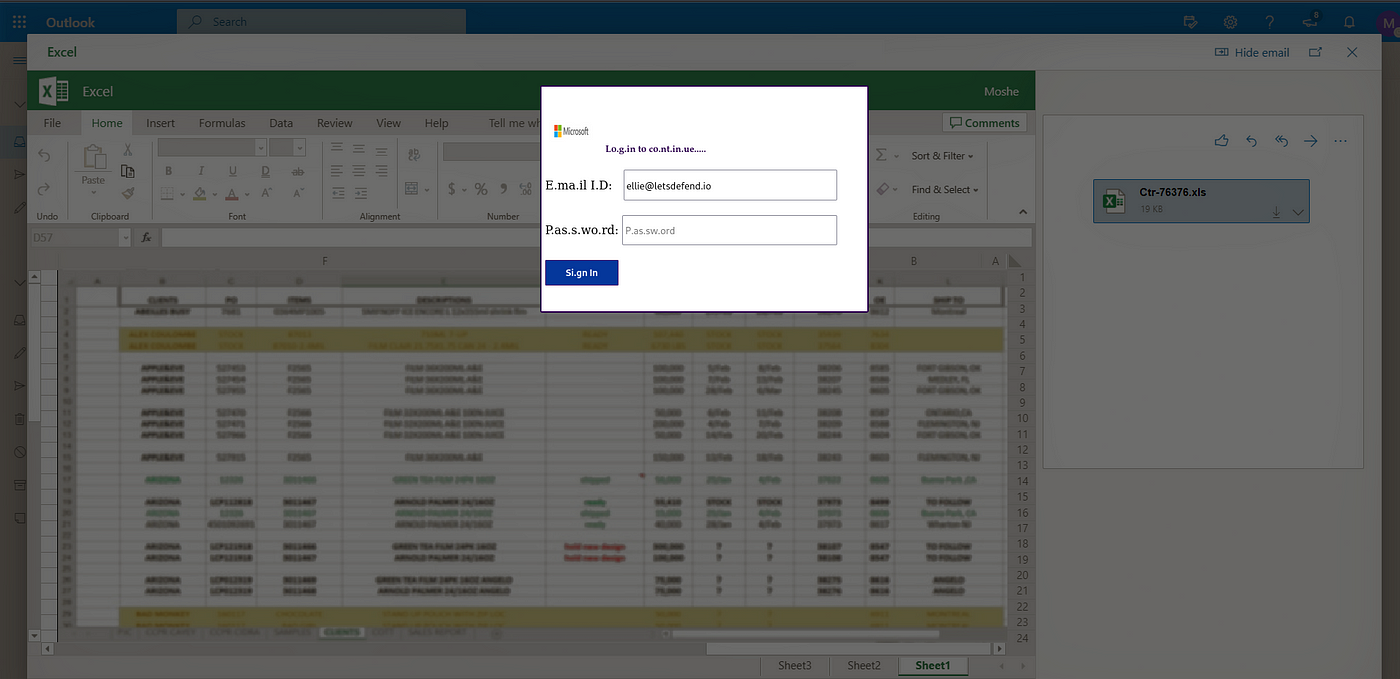
LetsDefend.io SOC-143 Password Stealer Walkthrough, by FarisArch
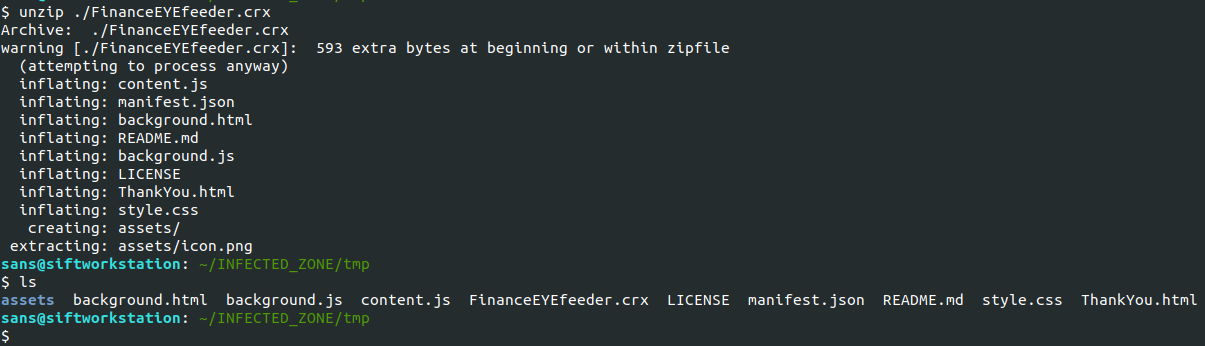
LetsDefend's Malware Analysis: Suspicious Browser Extension Walk-Through - Cyber Gladius

Password vulnerability at Fortune 1000 companies - Help Net Security
API4:2019 — Dictionary Attack. Hello all, today we will be looking…, by Shivam Bathla

LetsDefend's Malware Analysis: Suspicious Browser Extension Walk-Through - Cyber Gladius

Abdul Malik Mohammed on LinkedIn: Introduction to 802.1x with EAP-TLS

LetsDefend - Blue Team Training Platform
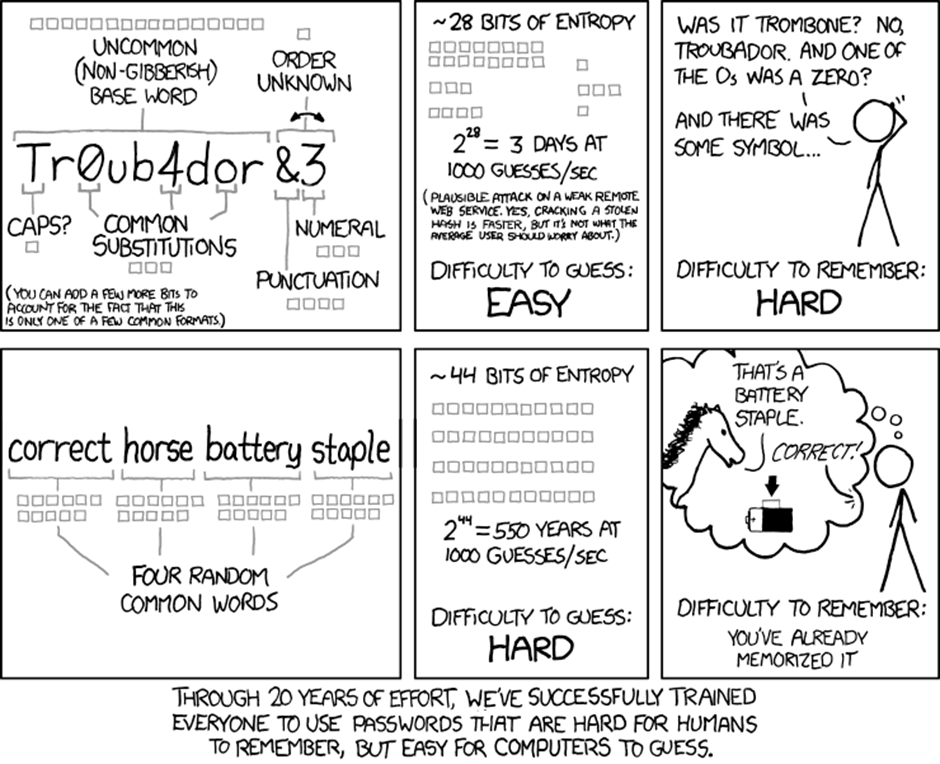
Three Word Passwords

Expanding digital forensics education with artifact curation and scalable, accessible exercises via the Artifact Genome Project - ScienceDirect

letsdefend.io challenge — Malicious Doc, by Enes Adışen

Expanding digital forensics education with artifact curation and scalable, accessible exercises via the Artifact Genome Project - ScienceDirect

LetsDefend: Hijacked NPM Package/Supply Chain Compromise, by Michael Koczwara
LetsDefend: Dynamic Malware Analysis Part 1, by Cybertech Maven

Edgar Castañeda 🧑💻 (@edgrcas) / X
de
por adulto (o preço varia de acordo com o tamanho do grupo)