Attackers use dynamic code loading to bypass Google Play store's
Descrição
Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

Deadglyph, a very sophisticated and unknown backdoor targets the
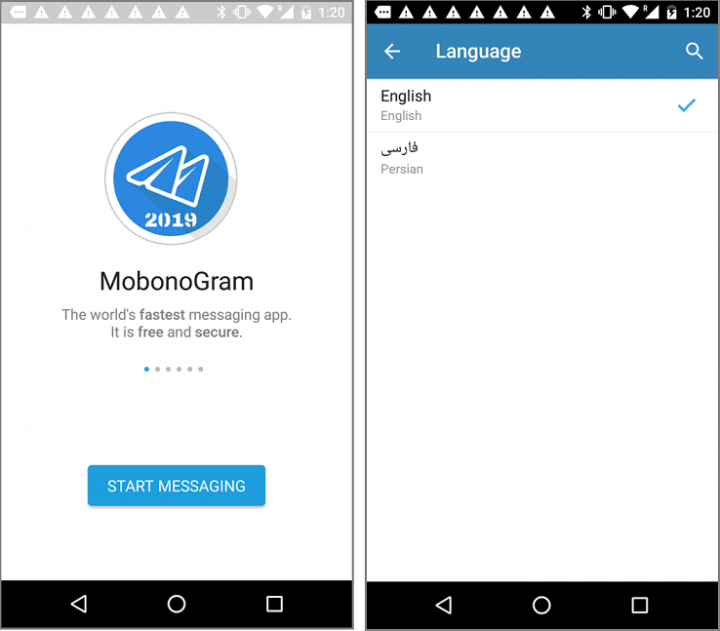
Unofficial Telegram App Secretly Loads Infinite Malicious Sites

Cyble — Hydra Android Malware Distributed Via Play Store

What Is Rootkit?

WakeUp Wednesday » Tesorion Cybersecurity Solutions

Quash EDR/XDR Exploits With These Countermeasures

This is how malicious Android apps avoid Google's security vetting

Google says attackers are still using versioning to bypass Play

Here's why the Google Play Store is a malware infected hellscape
Google Chrome - Wikipedia

Google explains how Android malware slips onto Google Play Store

Appdome How to Use Appdome MOBILEBot™ Defense

Google Play Store, Breaking Cybersecurity News

BrainTest - A New Level of Sophistication in Mobile Malware
de
por adulto (o preço varia de acordo com o tamanho do grupo)



/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/P/5/XFCwj8RF6CYgZ6m2jlQw/2011-05-19-ac-revelations-1.jpg)


