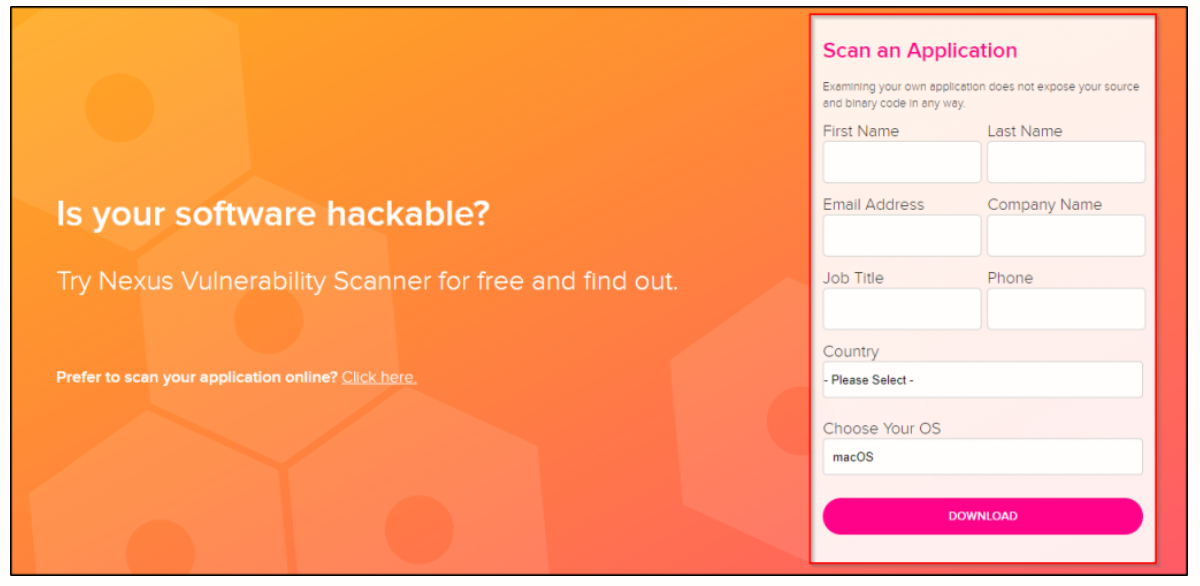
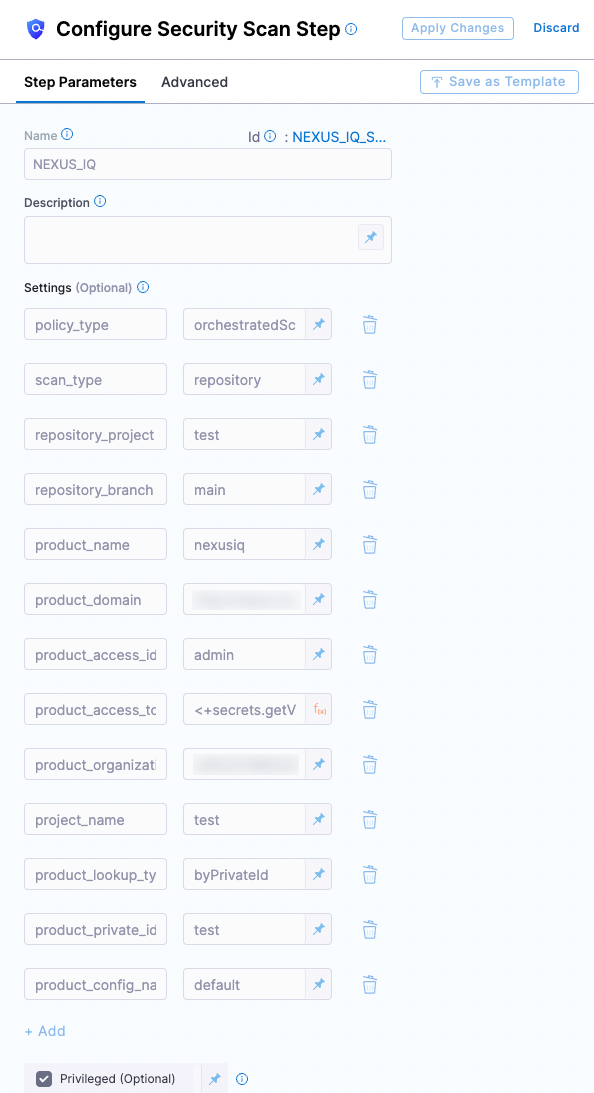
Vulnerability Scanning in your CI/CD Pipeline - Part Two
Descrição

Adding Image Scanning into your CI/CD Pipeline
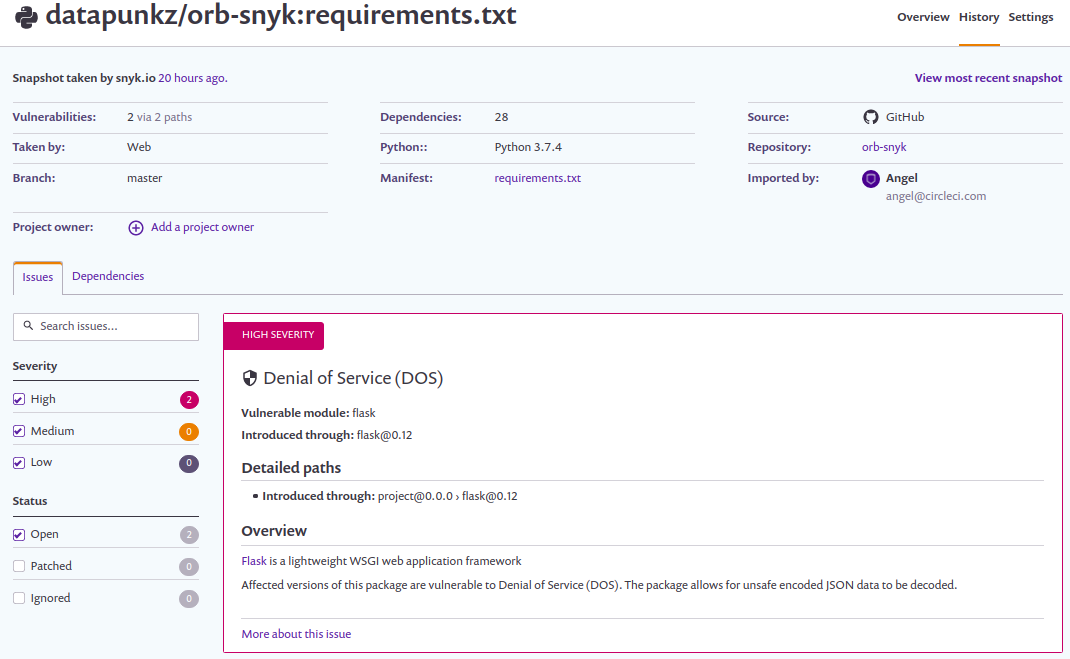
Adding application and image scans to your CI/CD pipeline

Building a security-conscious CI/CD pipeline
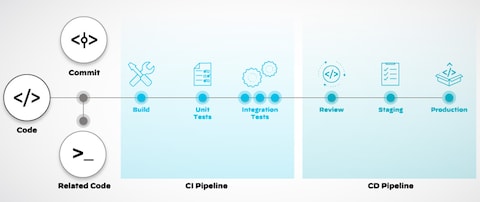
What Is the CI/CD Pipeline? - Palo Alto Networks

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub
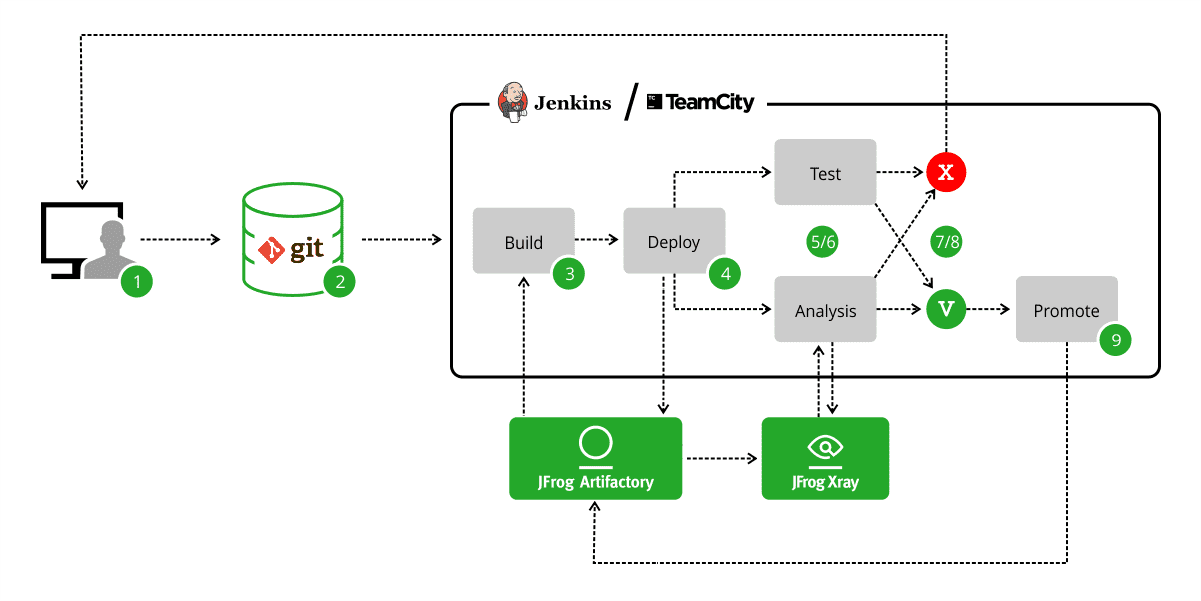
Security vulnerability detection scan for CI/CD pipeline with JFrog Xray
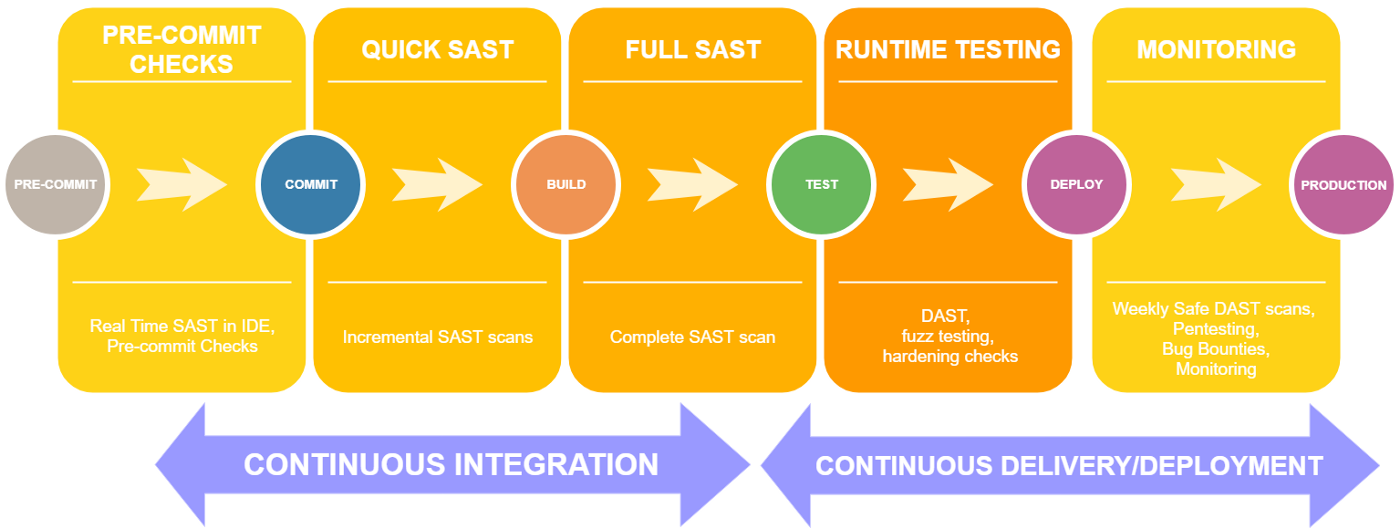
Integrating Web Vulnerability Scanners in Continuous Integration: DAST for CI/CD — Probely

Scan for vulnerabilities early to shift security left in CI/CD

Vulnerability scans on Kubernetes with Pipeline

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub

Vulnerability Scanning in your CI/CD Pipeline - Part Two
de
por adulto (o preço varia de acordo com o tamanho do grupo)