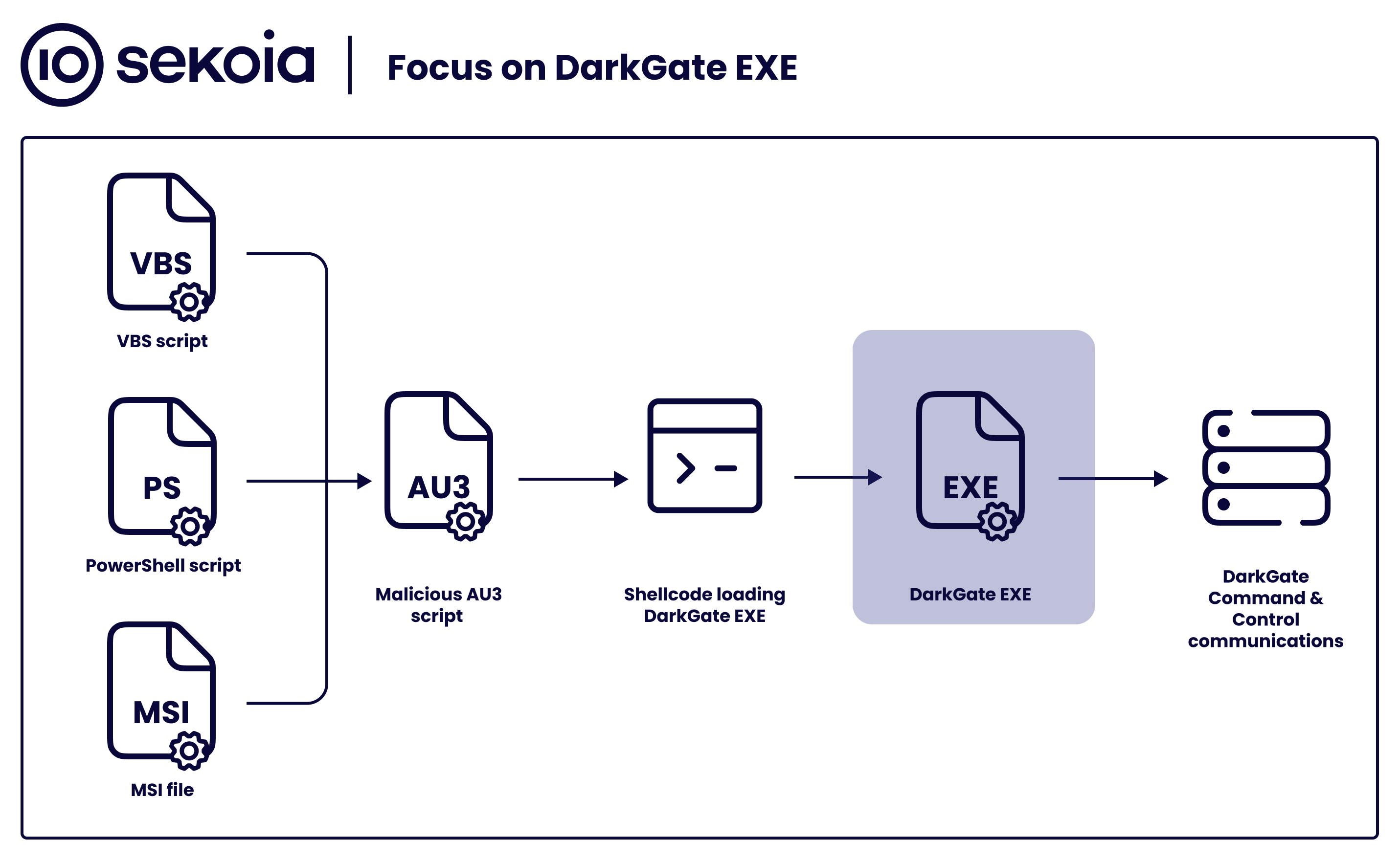
Major surge in memory-based attacks as hackers evade traditional
Descrição
Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

What is Malware? - Types, Examples, and Prevention
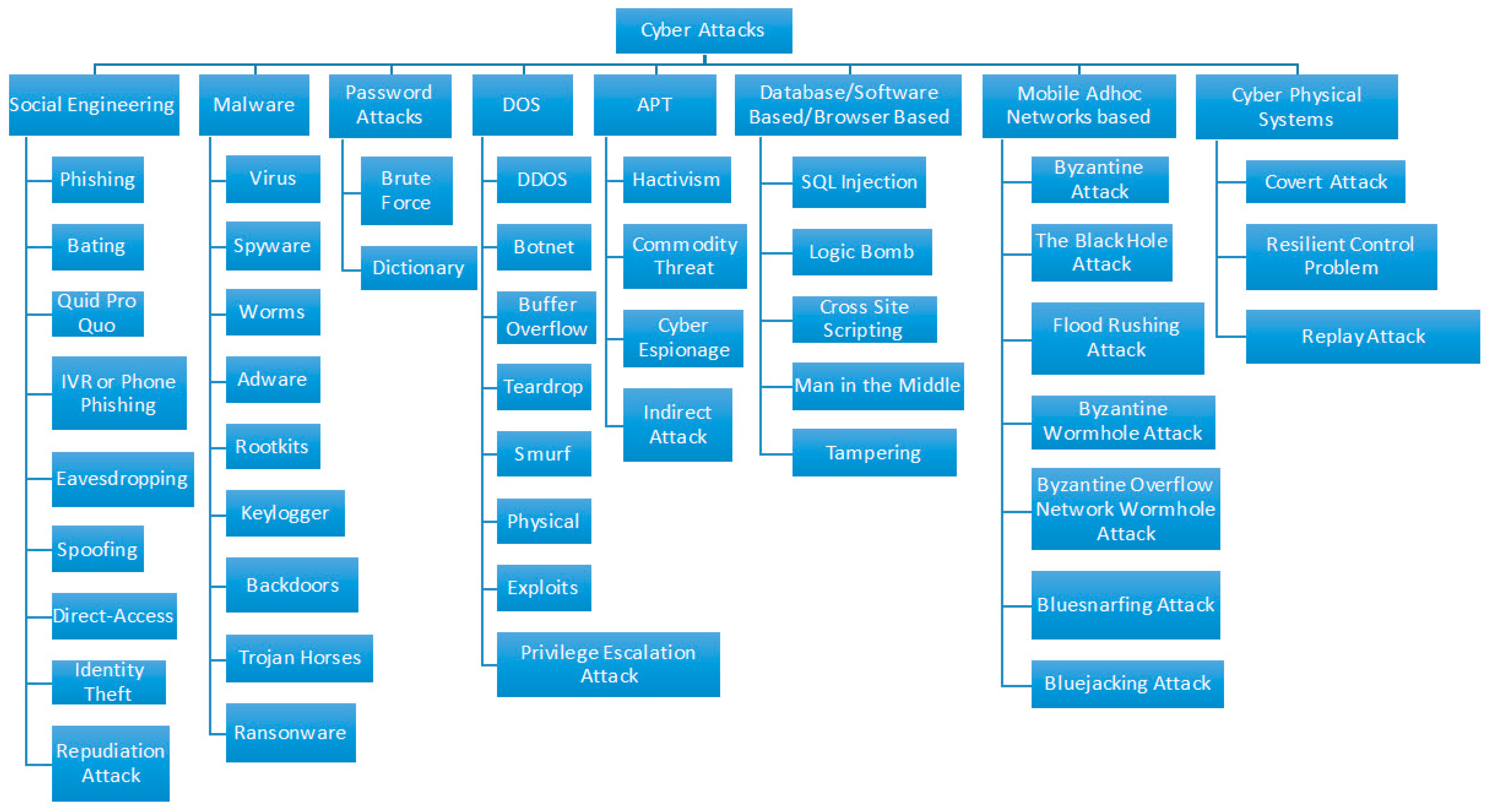
JCP, Free Full-Text

Types of Cyber Attacks You Should Be Aware of in 2024

Outsmarting Generative-AI Attacks: The Power of Automated Moving

Heuristic-based malware detection schema.

The Evolution of Cyber Threats

India Malware Attacks: India sees 31% surge in malware attacks in
Check Point Research reports a large-scale phishing attack
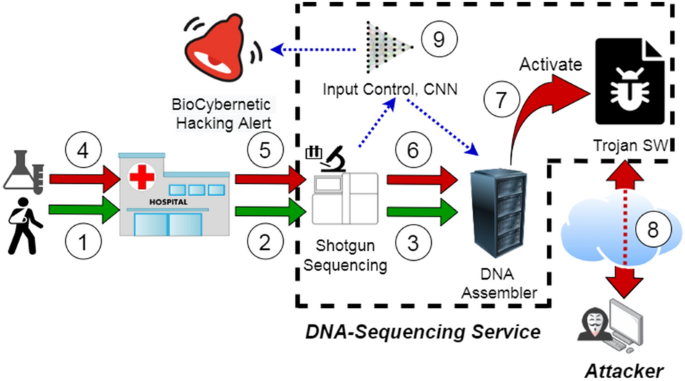
Using deep learning to detect digitally encoded DNA trigger for
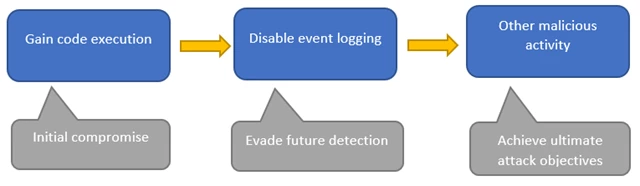
Detecting in-memory attacks with Sysmon and Azure Security Center
de
por adulto (o preço varia de acordo com o tamanho do grupo)