How hackers use idle scans in port scan attacks
Descrição
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

Port scanners

Nmap cheat sheet: From discovery to exploits, part 2: Advance port scanning with Nmap and custom idle scan
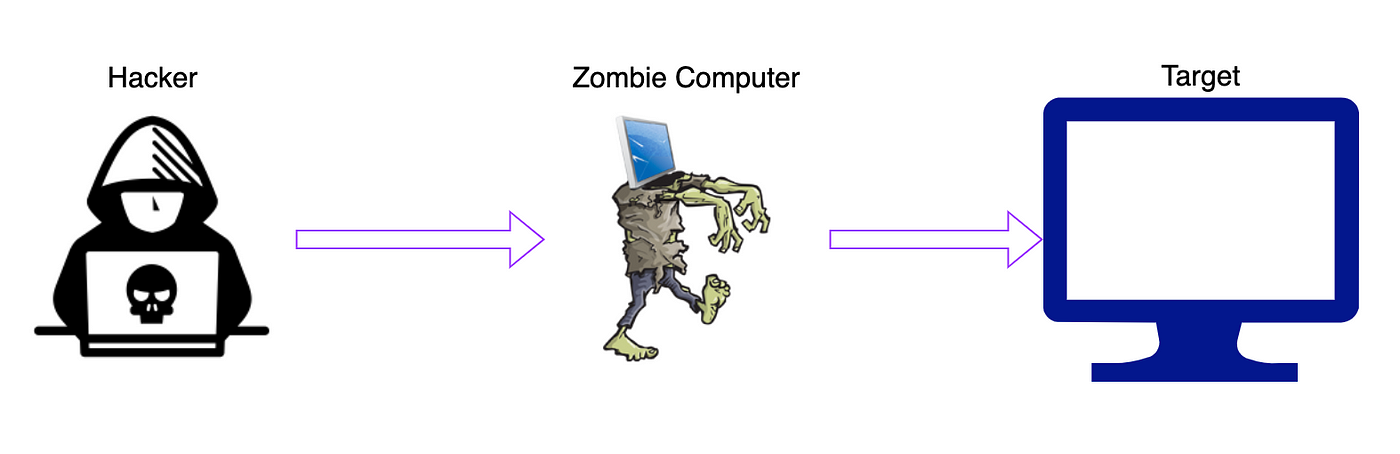
Zombie/Idle scan working principle, by NGU

A Complete Guide to Nmap, Nmap Tutorial
PDF) Port Scanning: Techniques, Tools and Detection

№2. Ethical Hacking Labs. Network scanning - HackYourMom
How To Defend Against Port Scan Attacks
What Is Nmap? A Comprehensive Tutorial For Network Mapping
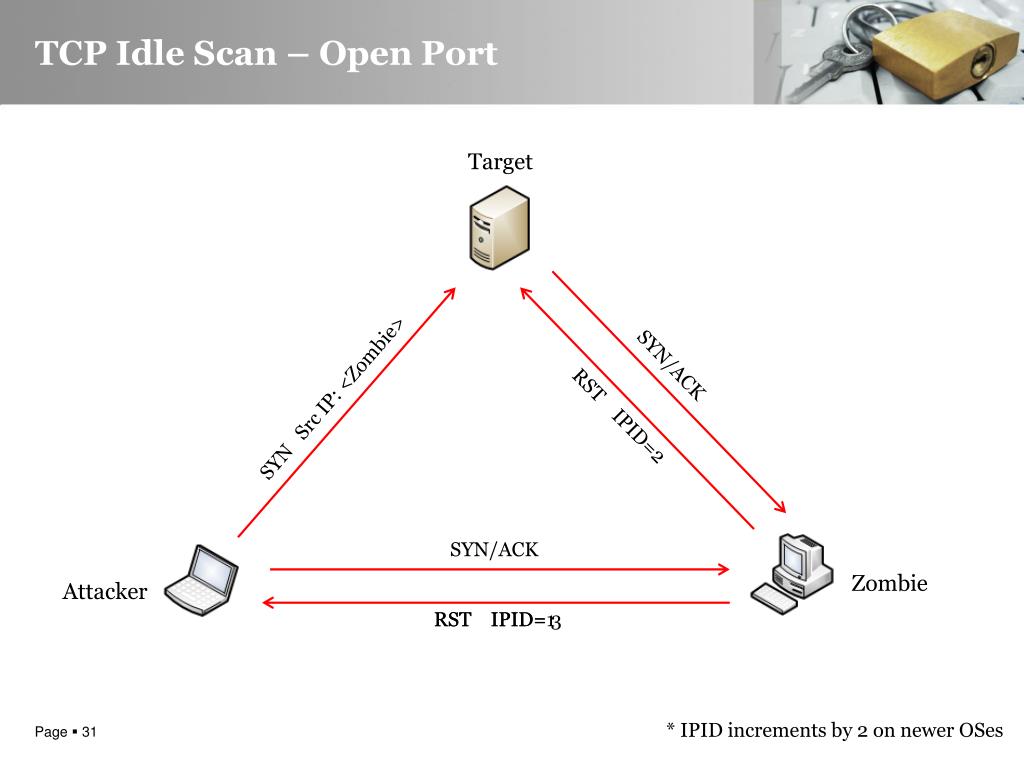
PPT - Advanced Idle Scanning PowerPoint Presentation, free download - ID:5241398
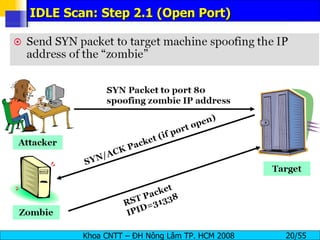
Module 3 Scanning

What is a Port Scanner and How Does it Work?
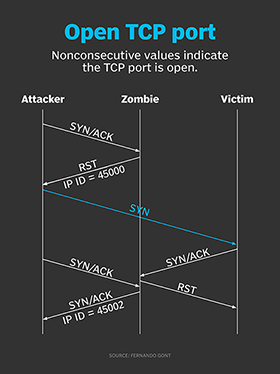
How hackers use idle scans in port scan attacks
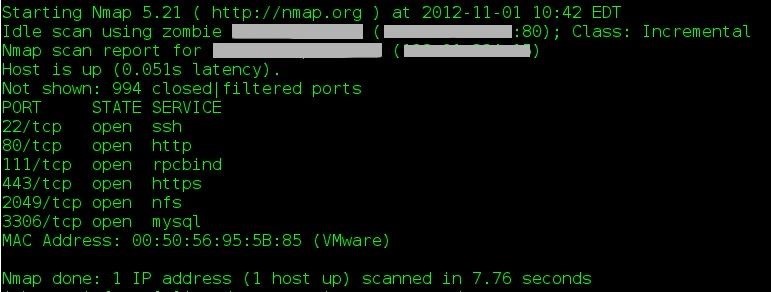
How to Do an Idle Scan with Nmap « Null Byte :: WonderHowTo
de
por adulto (o preço varia de acordo com o tamanho do grupo)