System, error, attack, malware, failure, unauthorized, hacker icon
Descrição
Download this system, error, attack, malware, failure, unauthorized, hacker icon in filled outline style. Available in PNG and SVG formats.

What are social engineering attacks?
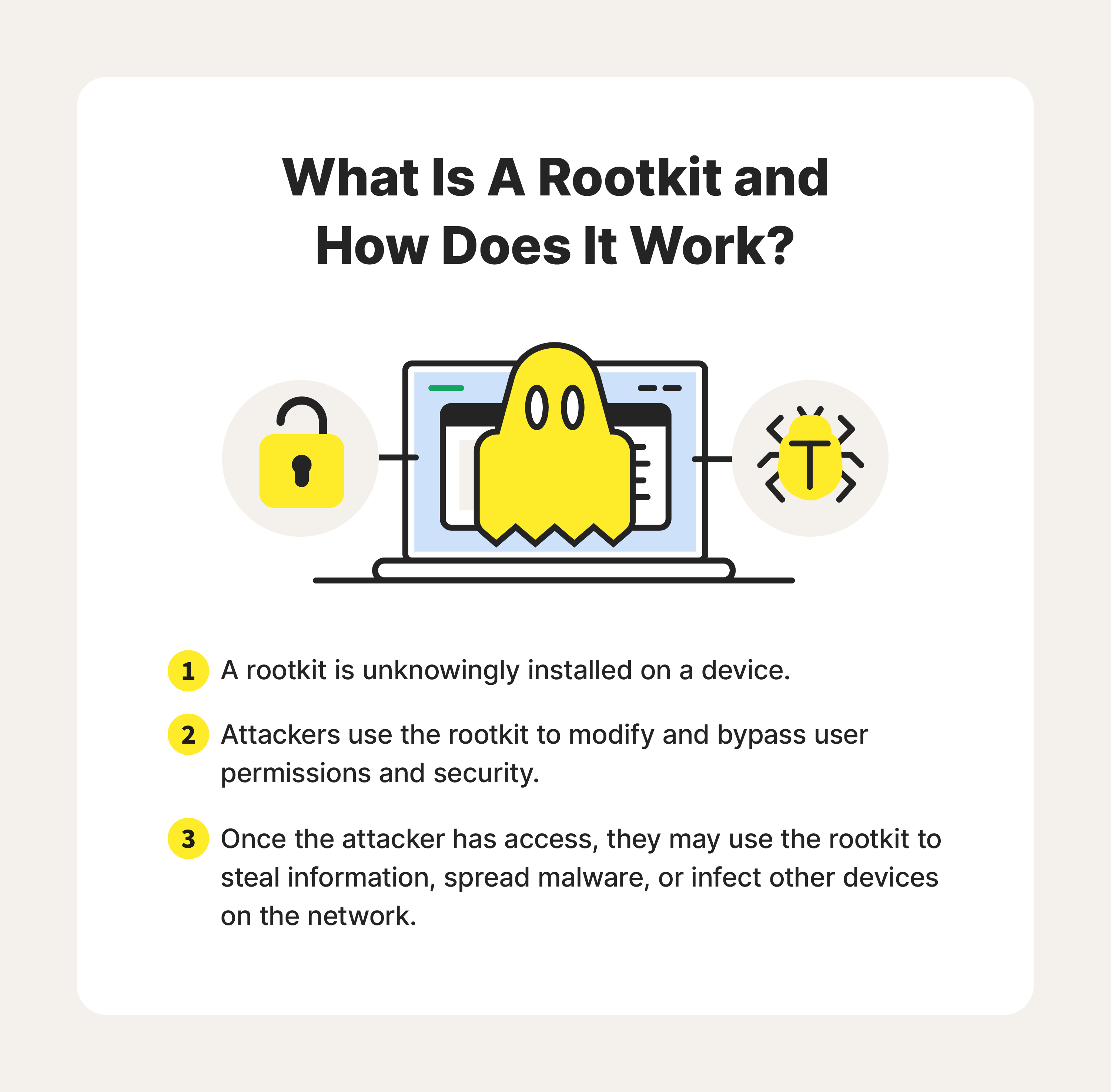
What is a rootkit? Detection + prevention tips - Norton

Firmware Attacks: What They Are & How I Can Protect Myself

67. Unauthorized Access Warning Notification on Digital Security
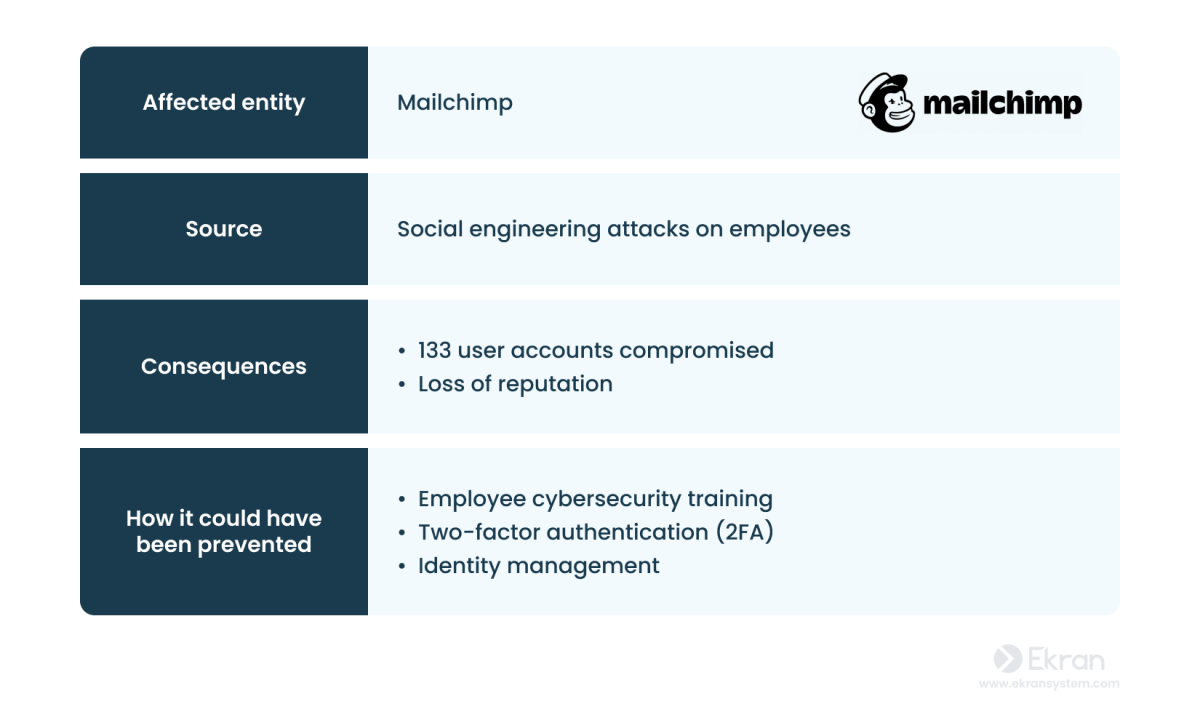
7 Real-Life Data Breaches Caused by Insider Threats

How Hackers Use Social Engineering to Spread Dridex Malware

Most Common Hacking Techniques

What is an Attack Vector? 15 Common Attack Vectors to Know
5,200+ Hacker Attack Stock Videos and Royalty-Free Footage
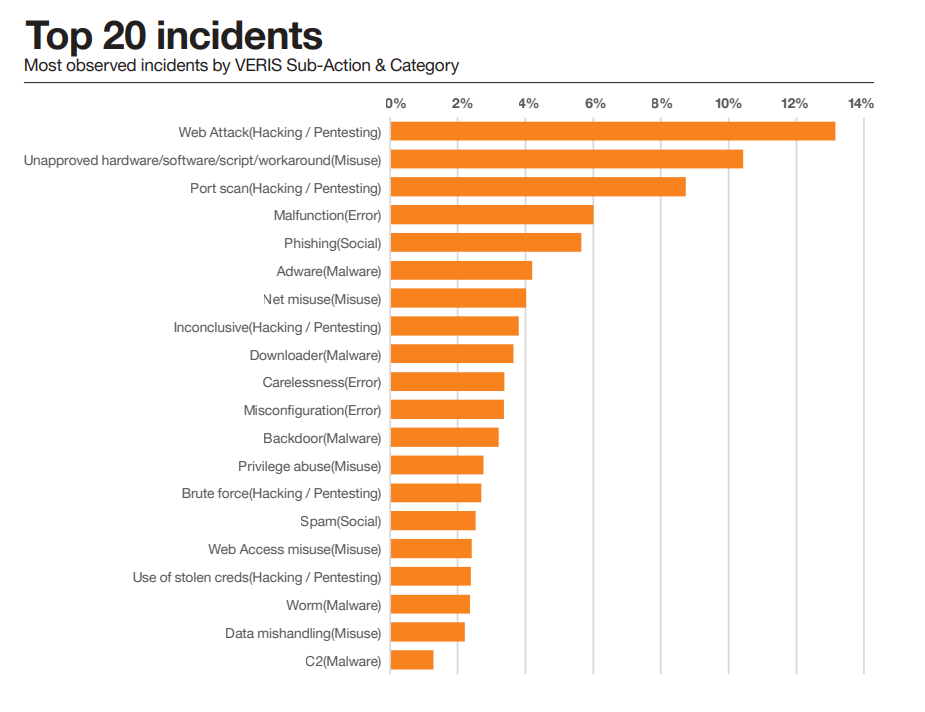
Security Misconfigurations Caused 35% of All Time Cyber Incidents

Wi-Fi Authentication problems: Causes and solutions

600+ Stop Hackers Stock Photos, Pictures & Royalty-Free Images

17 Most Common Types of Cyber Attacks & Examples (2024)

A massive campaign delivered a proxy server application to 400,000
de
por adulto (o preço varia de acordo com o tamanho do grupo)