The SpiKey attack: How to copy keys using sound
Descrição
The SpiKey attack: How one can copy a key using a phone recording of the sound of the clicks the key makes during insertion into a lock.
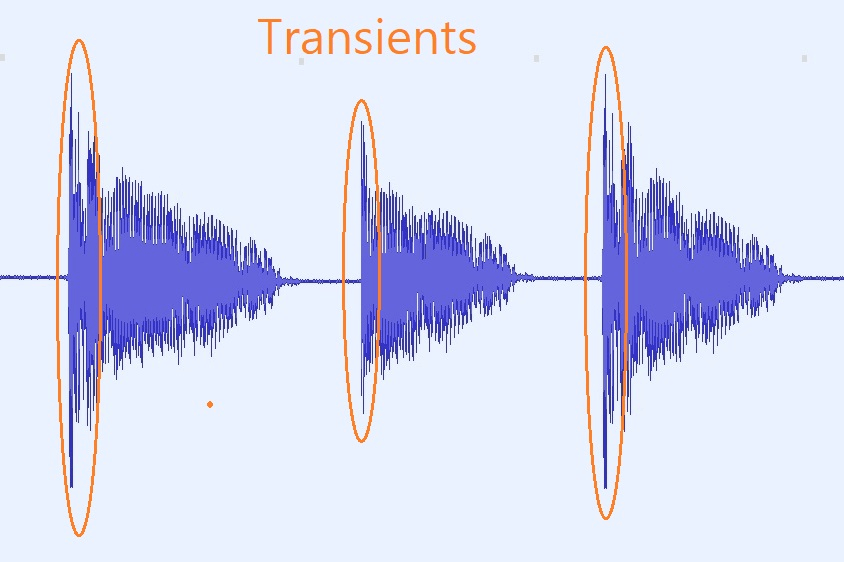
What are transients? How to deal with it in the mixing proces?
How to expedite your investigations with a DFIR - Cynet

HM-2: The Sound of Swedish Death Metal and Beyond - BOSS Articles

Why are mRNA vaccines so exciting? - Harvard Health

Hackers can now clone your keys just by listening to them with a smartphone

AI Can Now Crack Your Password by 'Listening' to Your Keyboard Sounds
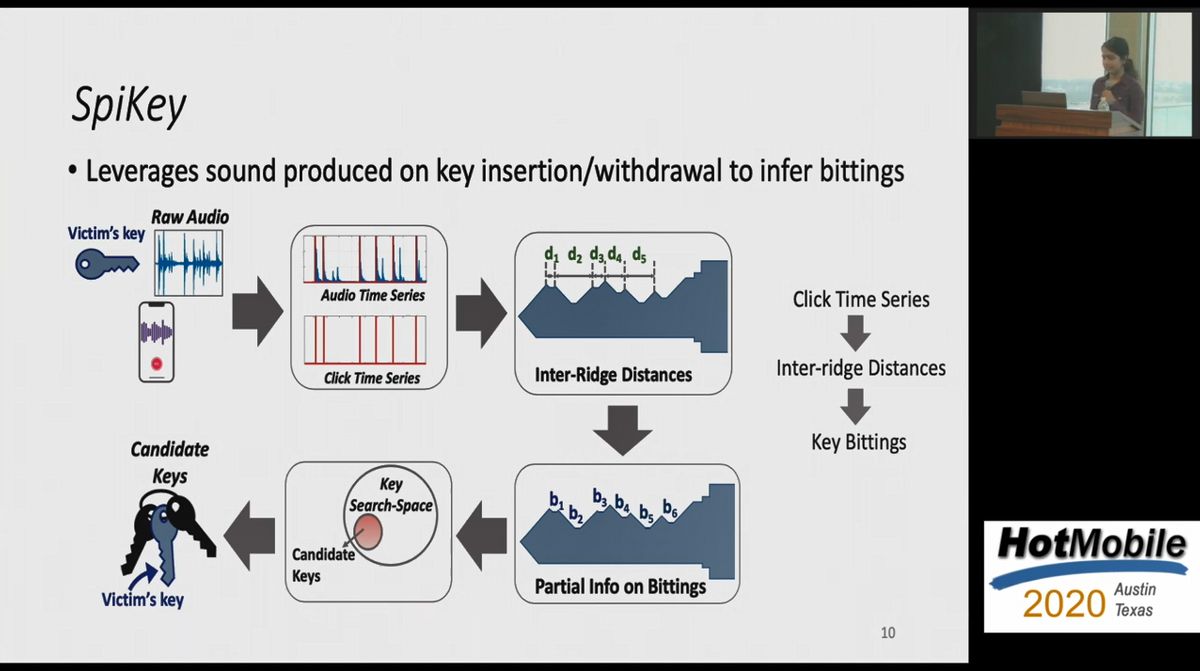
Researchers warn that there is a danger that a duplicate key will be made from 'sound when inserting a key into a keyhole' - GIGAZINE

What is Malware? Malware Definition, Types and Protection

Spectrasonics - Omnisphere 2.8 - Library
de
por adulto (o preço varia de acordo com o tamanho do grupo)