Cmd Hijack - a command/argument confusion with path traversal in
Descrição
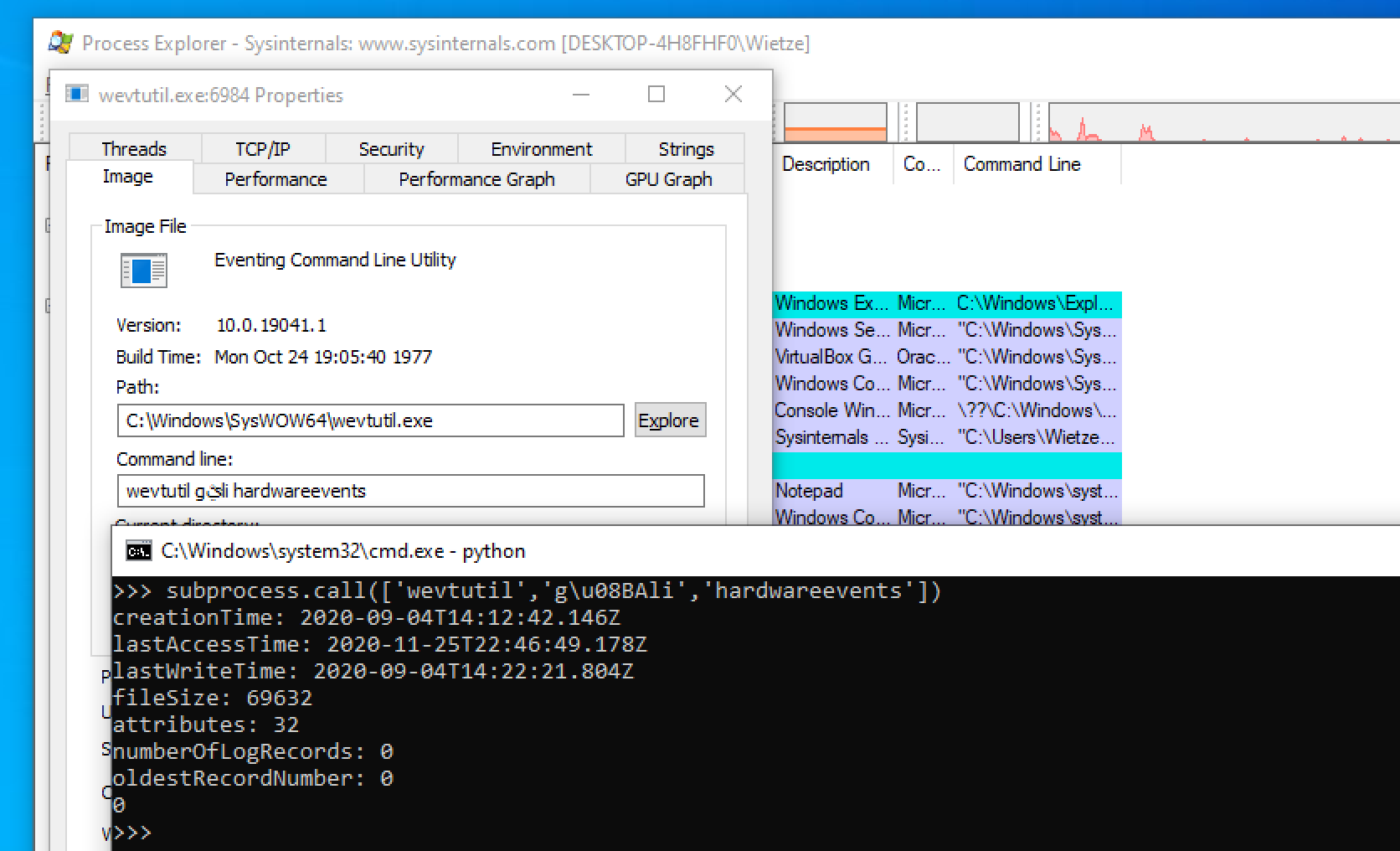
This one is about an interesting behavior 🤭 I identified in cmd.exe in result of many weeks of intermittent (private time, every now and then) research in pursuit of some new OS Command Injection attack vectors.
So I was mostly trying to:
* find an encoding missmatch between some command check/sanitization code and the rest of the program, allowing to smuggle the ASCII version of the existing command separators in the second byte of a wide char (for a moment I believed I had it in the StripQ
Achieving Remote Code Execution in Steam: a journey into the
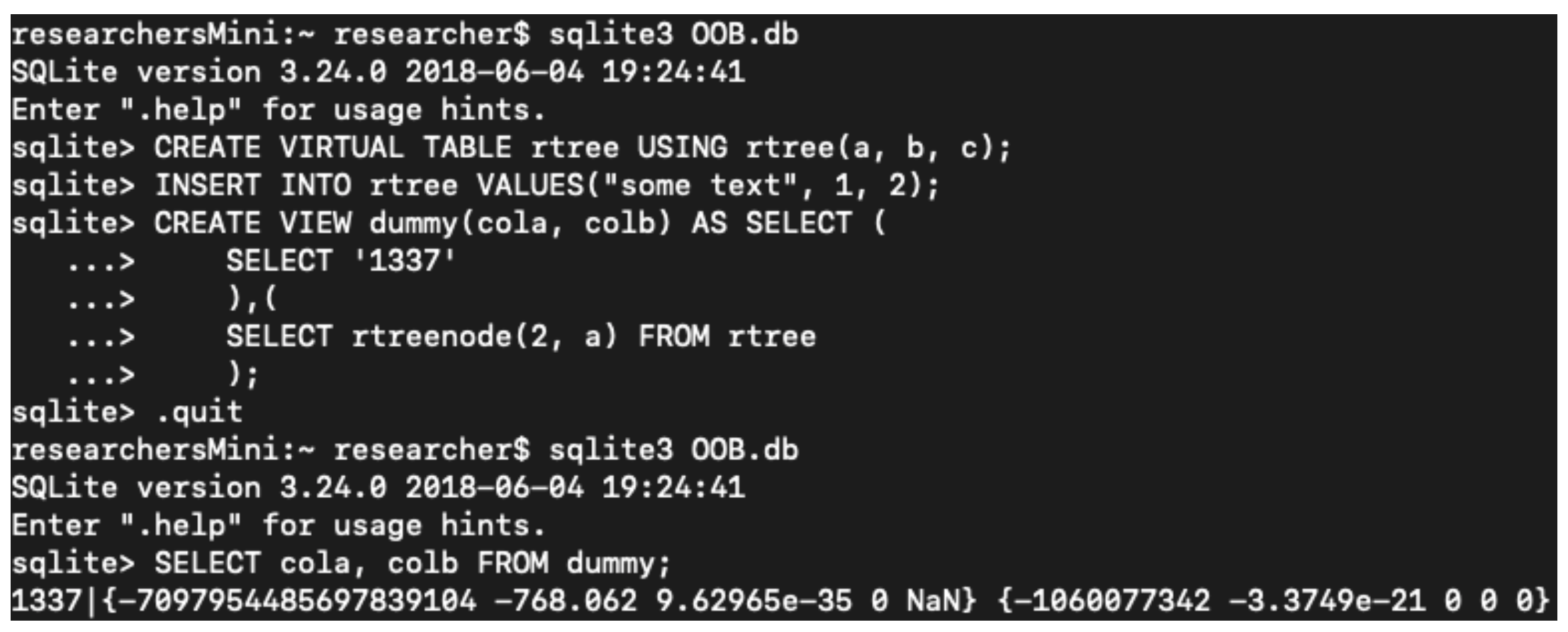
SELECT code_execution FROM * USING SQLite; - Check Point Research

Bug Bytes #75 - NahamCon, ServiceNow misconfigurations & Creating

35 Best Windows Software Of Year 2014 : r/windows

Automatic Exploit Generation, February 2014

Cmd Hijack - a command/argument confusion with path traversal in

0xdf hacks stuff CTF solutions, malware analysis, home lab
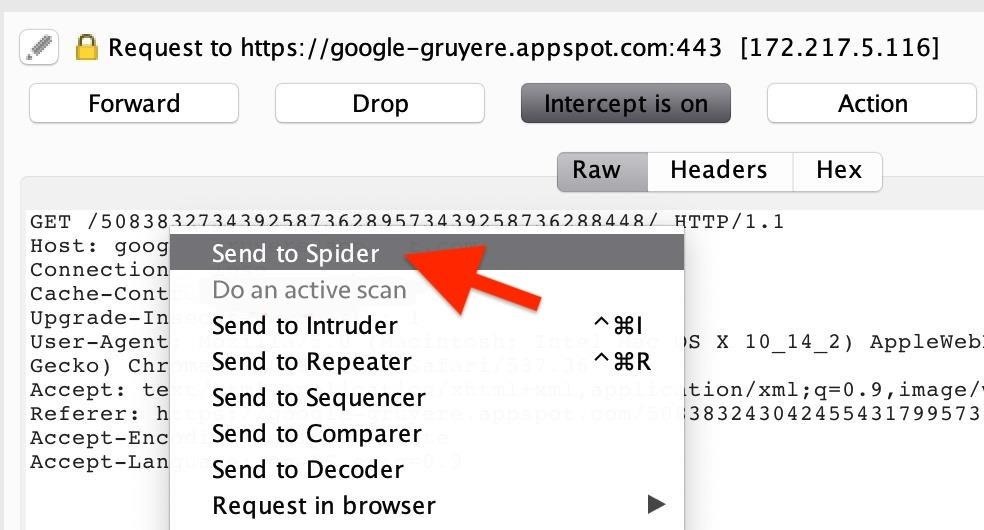
How to Leverage a Directory Traversal Vulnerability into Code
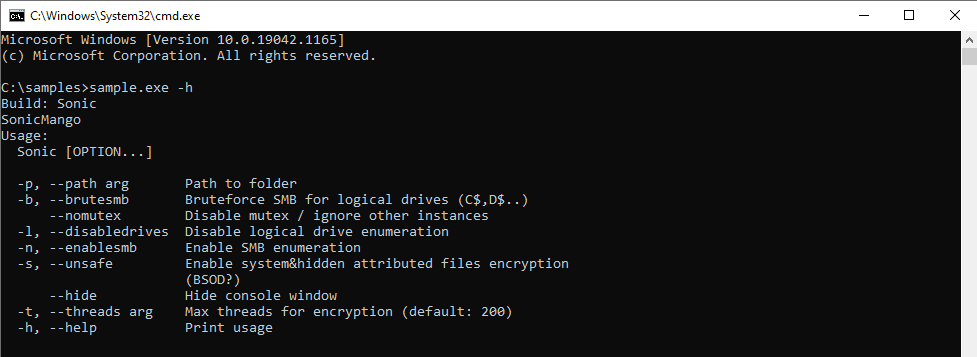
AvosLocker Ransomware Behavior Examined on Windows & Linux

Cmd Hijack - a command/argument confusion with path traversal in

Live Updates: SolarWinds Supply Chain Attack

Cmd Hijack - a command/argument confusion with path traversal in
Exploit Development: Browser Exploitation on Windows - CVE-2019

Achieving Remote Code Execution in Steam: a journey into the
de
por adulto (o preço varia de acordo com o tamanho do grupo)