a1), {(b1)-(c1)}, (d1), (e1), and {(f1)-(g1)} shows copy-move forged
Descrição

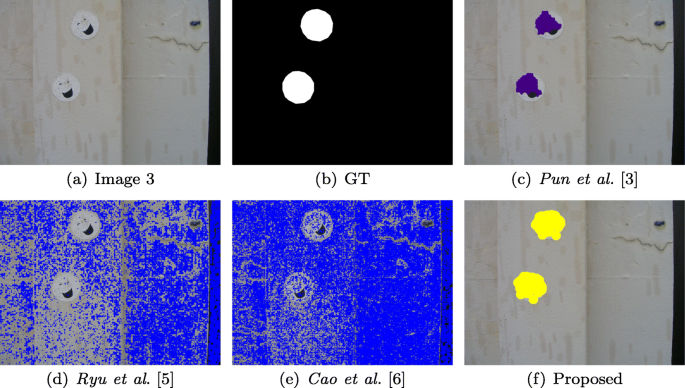
a1), (b1), (c1), (d1), (e1), and (f1) shows forged images with

Utilization of edge operators for localization of copy-move image forgery using WLD-HOG features with connected component labeling
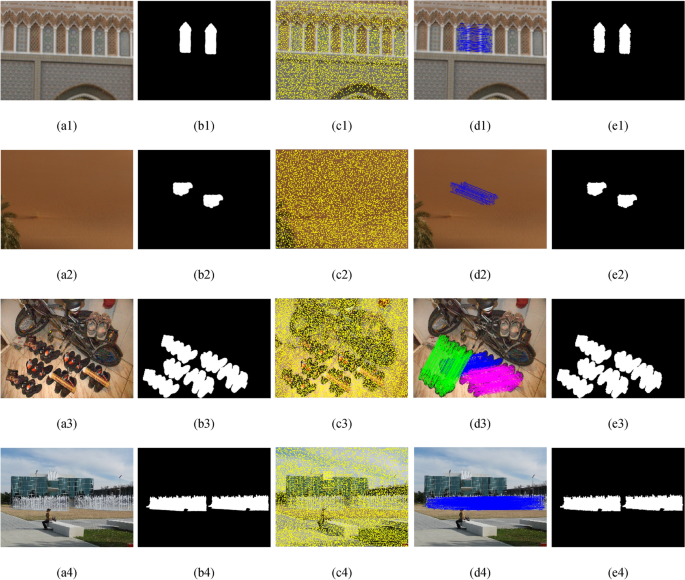
Robust and effective multiple copy-move forgeries detection and localization
The first five examples for Copy-Move forgery detection: original

Week 1 — Copy Move Forgery Detection, by Eflatun Doğa AYDIN, BBM406 Spring 2021 Projects
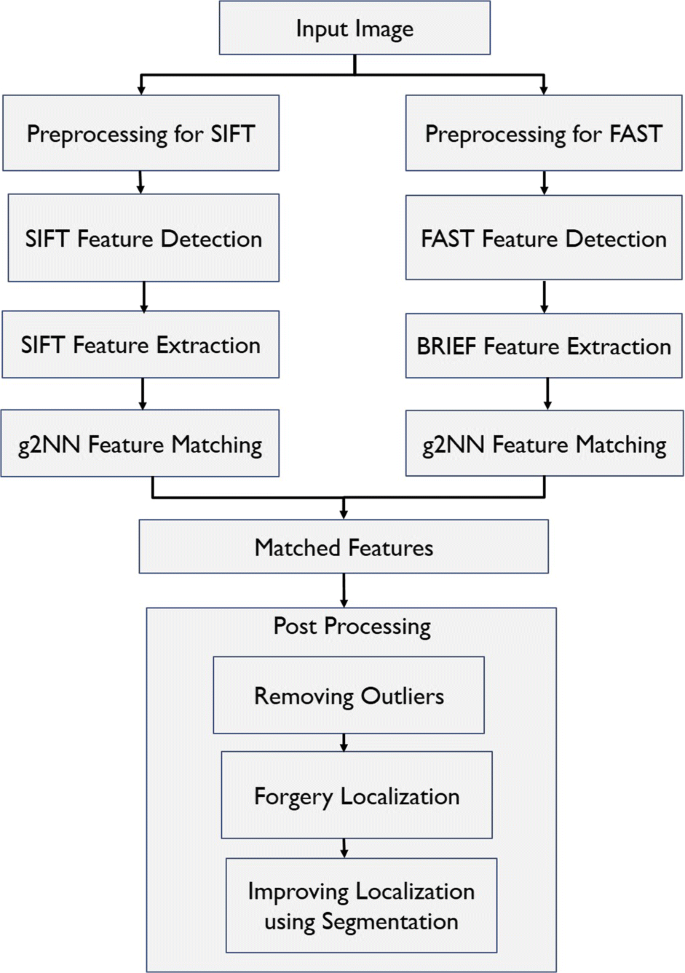
FAST, BRIEF and SIFT based image copy-move forgery detection technique
FAST, BRIEF and SIFT based image copy-move forgery detection technique

Copy Move Image Forgery, PDF, Accuracy And Precision
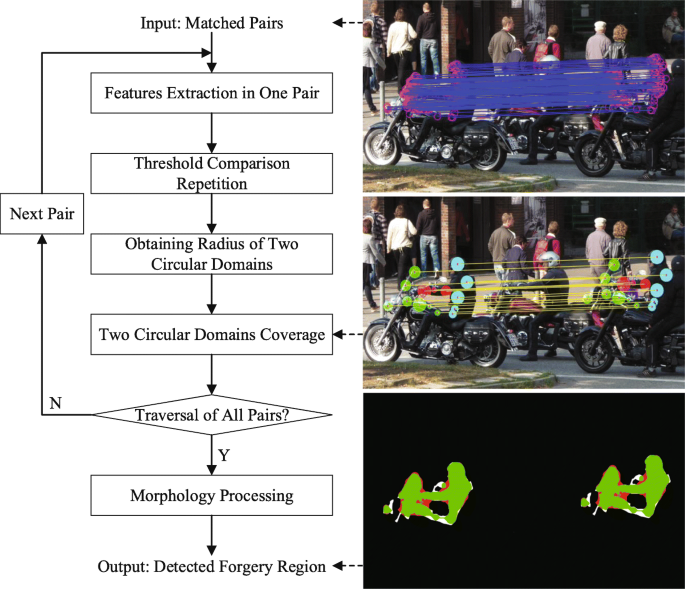
Copy-move image forgery detection based on evolving circular domains coverage
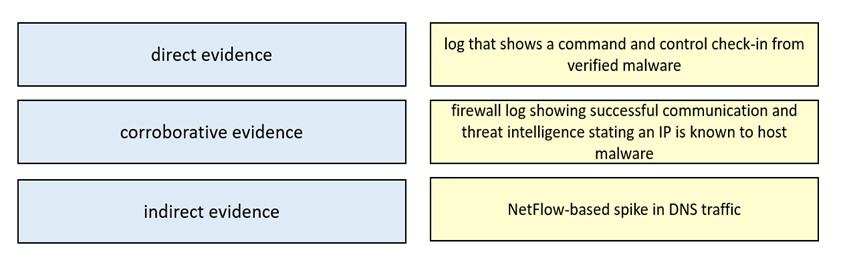
Exam 200-201 topic 1 question 117 discussion - ExamTopics
de
por adulto (o preço varia de acordo com o tamanho do grupo)