TrustedSec Playing With Old Hacks
Descrição

Raspberry Pi – Page 2 – CYBER ARMS – Computer Security
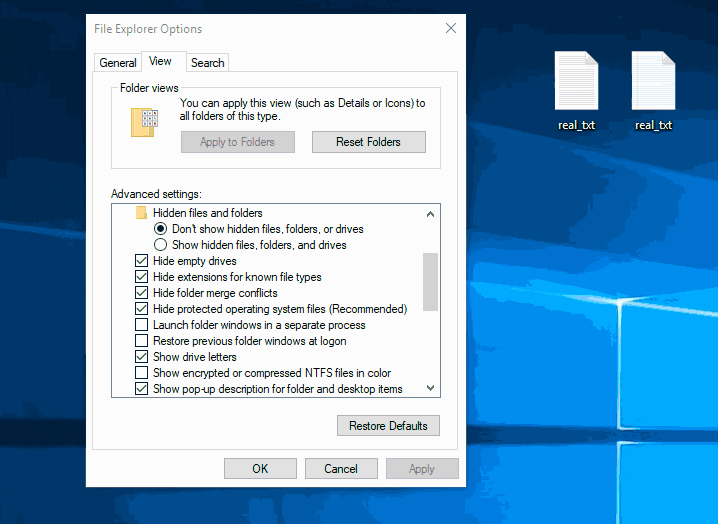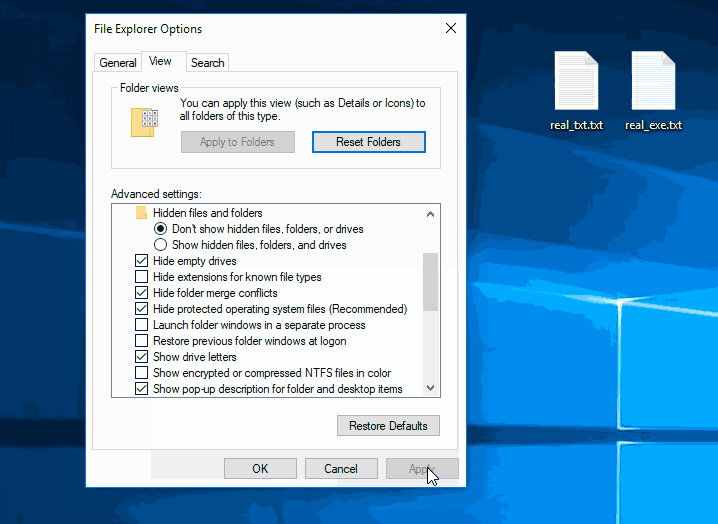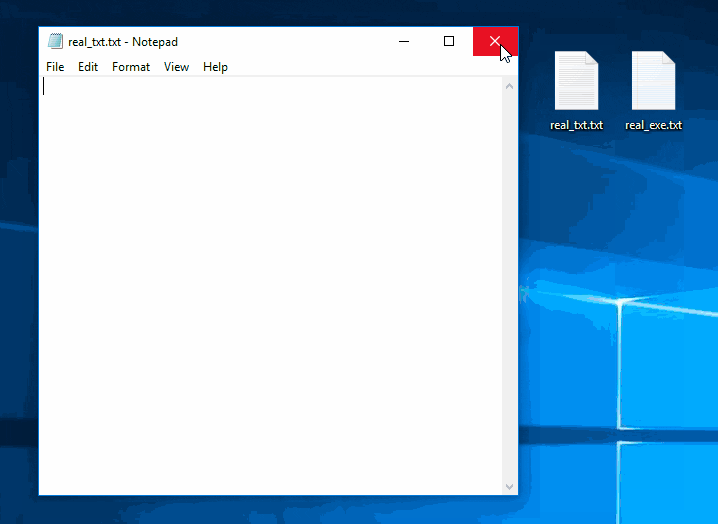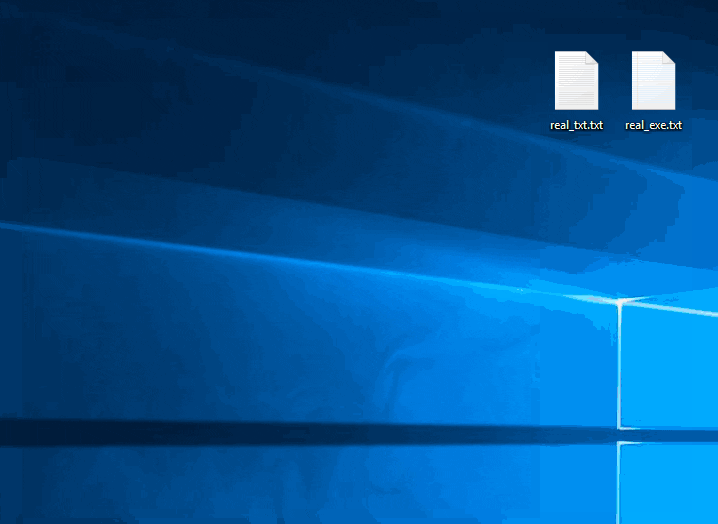
Hacking Windows 10: How to Create an Undetectable Payload, Part 1 (Bypassing Antivirus Software) « Null Byte :: WonderHowTo

Gaming the game: Popular video games can be vulnerable to hackers

Focus Lab®

Comcast Says Data of 36 Million Accounts Was Compromised in Breach - WSJ

Colonial Pipeline CEO Tells Why He Paid Hackers a $4.4 Million Ransom - WSJ

Hacker shares how easy it is for thieves to steal your passwords

TrustedSec Playing With Old Hacks
GitHub - trimstray/the-book-of-secret-knowledge: A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools and more.

TrustedSec Playing With Old Hacks
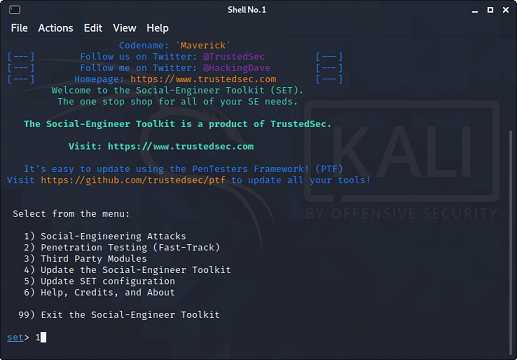
How to hack a Facebook account using Kali Linux - javatpoint

GitHub - A-poc/RedTeam-Tools: Tools and Techniques for Red Team / Penetration Testing

Hackers, Trolls, and Bots Ready For Election Day - TheStreet

TrustedSec Playing With Old Hacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)


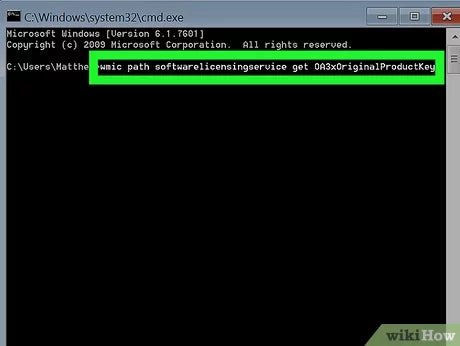
:max_bytes(150000):strip_icc()/help-command-windows-10-5235fec0871648538c84a171a37b33fd.png)



