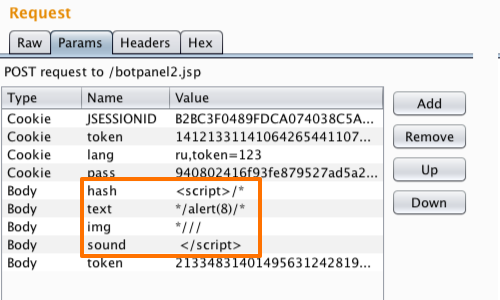
Transforming Self-XSS Into Exploitable XSS
Descrição
This blog is describes an attempt by a security researcher to exploit a Cross-site Scripting (XSS) vulnerability. It explains the importance of template strings in XSS filtering, how to overcome the document.domain issue, and the discovery and exploitation of Self-XSS, with reading suggestions.

Elevating Self XSS To Stored XSS Using This Super Simple Yet Often Missed Method

Transforming Self-XSS Into Exploitable XSS
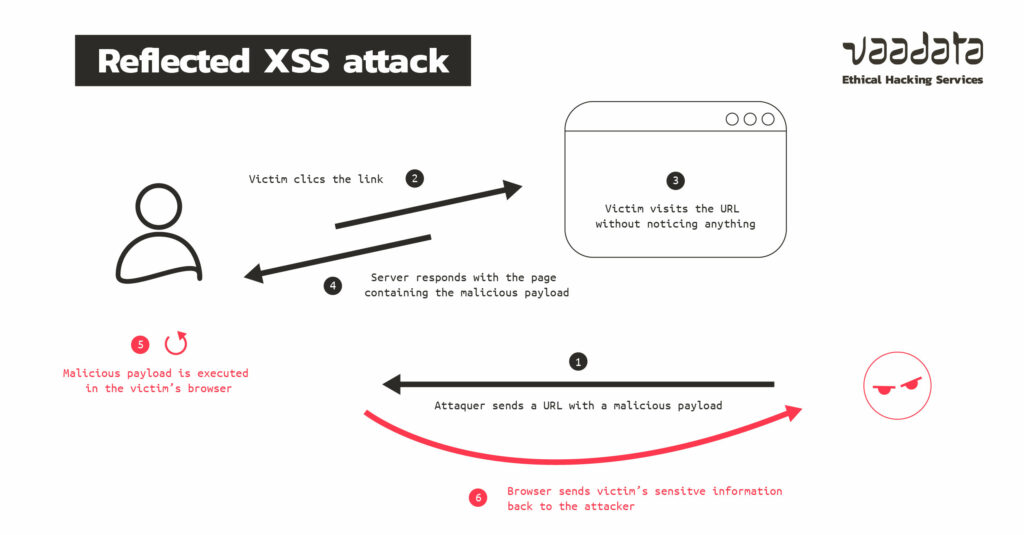
XSS: Principles, Attacks and Security Best Practices
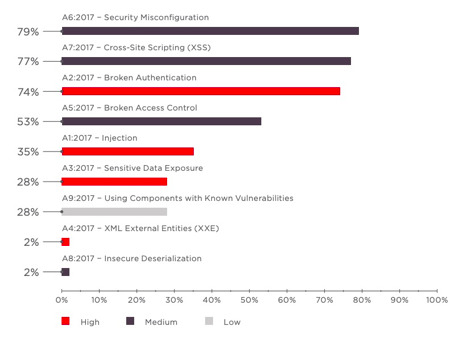
What is a Cross-Site Scripting (XSS) attack: Definition & Examples

Xss cheat sheets by DragoN JAR - Issuu
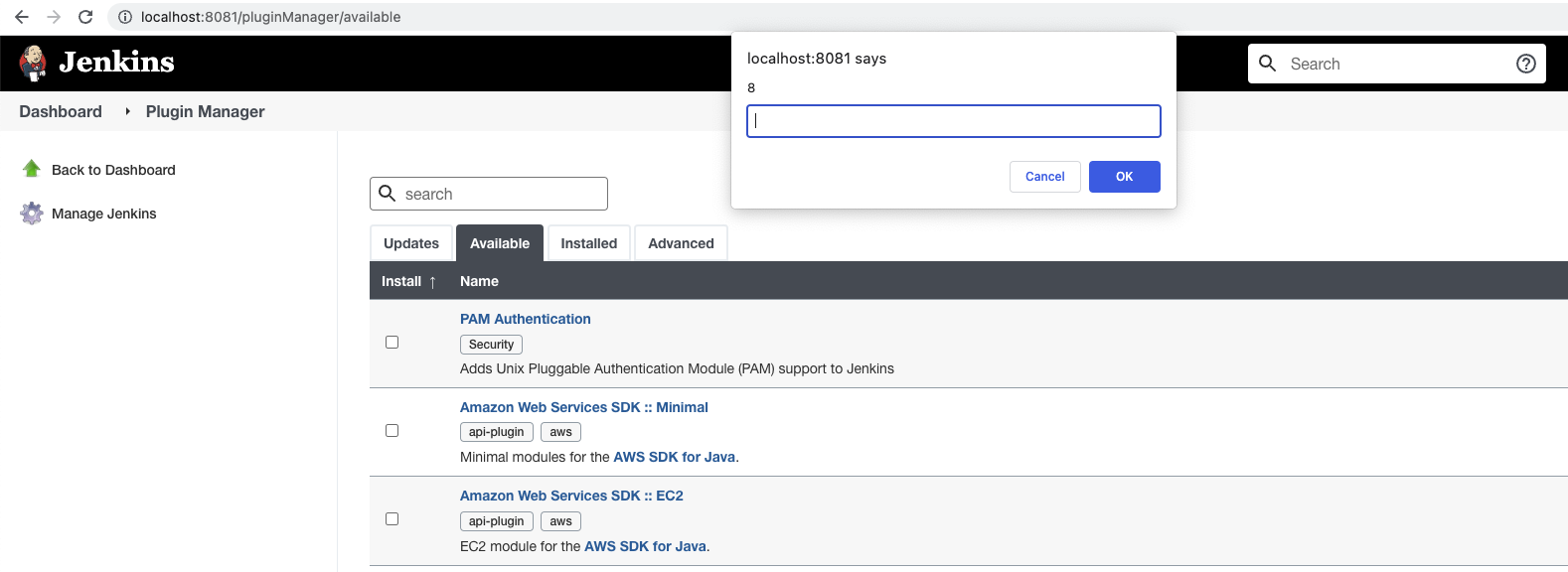
CorePlague: Critical Vulnerabilities in Jenkins Server Lead to RCE

Transforming Self-XSS Into Exploitable XSS

Transforming Self-XSS Into Exploitable XSS

Transforming Self-XSS Into Exploitable XSS
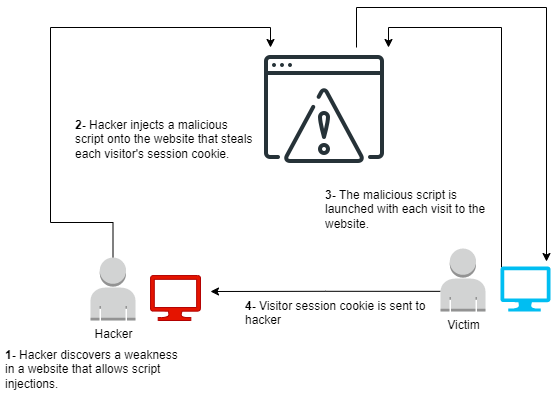
What is Cross-Site Scripting (XSS) Reflected Self Vulnerability?
js-xss/benchmark/file.html at master · leizongmin/js-xss · GitHub
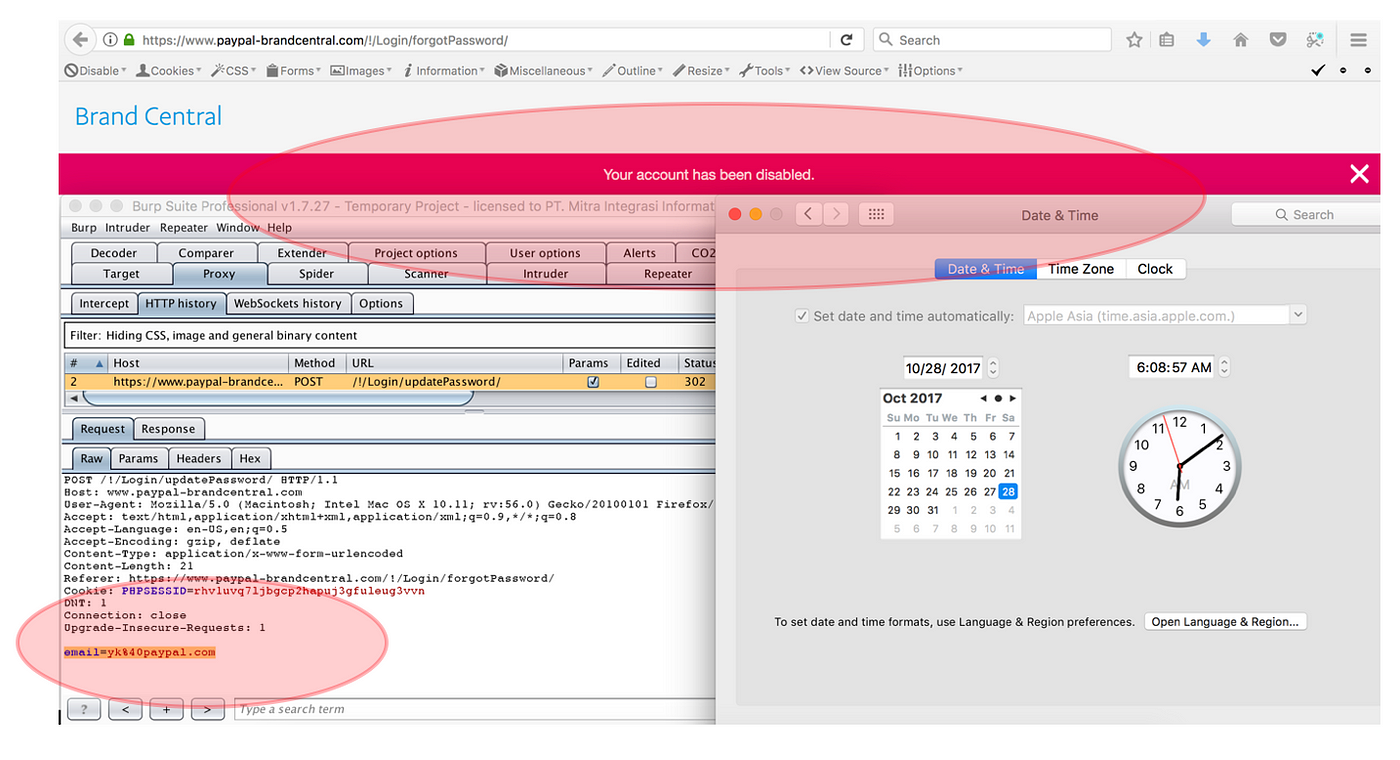
Turning Self-XSS into non-Self Stored-XSS via Authorization Issue at “PayPal Tech-Support and Brand Central Portal”, by YoKo Kho
de
por adulto (o preço varia de acordo com o tamanho do grupo)