SILKLOADER: How Hackers Evade Detection
Descrição
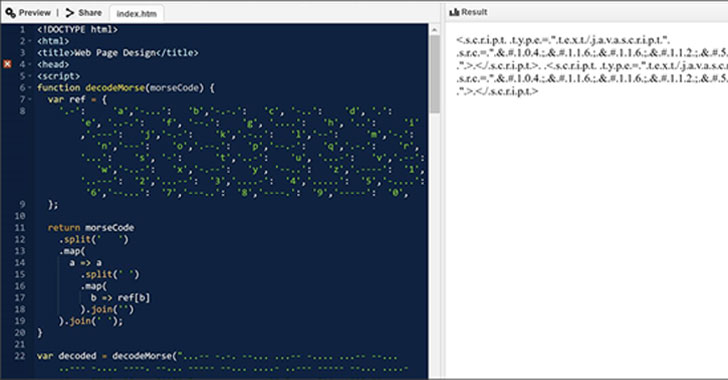
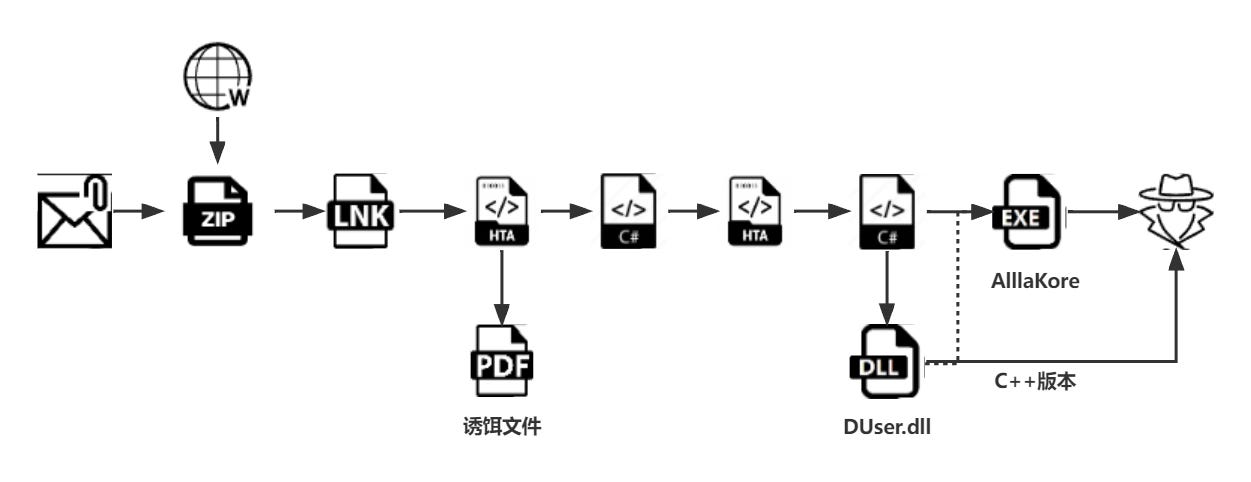
As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

Spyder Loader: Malware Seen in Recent Campaign Targeting Organizations in Hong Kong
Telerik Government breach, Critical Outlook bug, LockBit threatens SpaceX
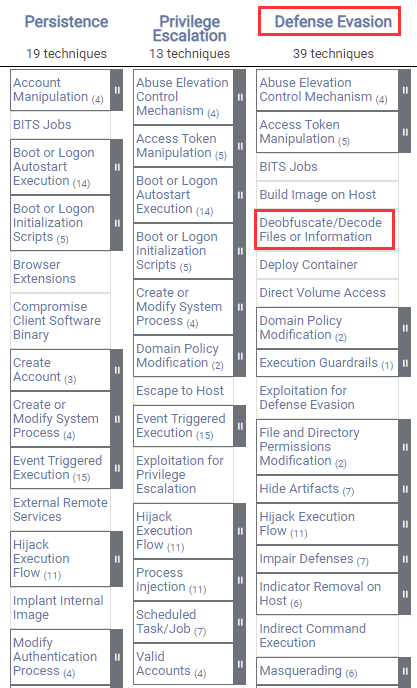
Windows Red Team Defense Evasion Techniques - HackerSploit Blog

Companies on alert after apparent hack of cloud-based security camera service

Lynx-CERT

Types of Evasion Technique For IDS - GeeksforGeeks

AV/EDR Evasion, Malware Development P-3

Spy Matrix Pro Sweep Anti Spy Detector - Bug Detector, Hidden Devices Detector - RF Detector for Hidden Cameras, GPS Trackers - Find Unwanted Devices : Electronics
Bluepurple Pulse: week ending March 26th - by Ollie
de
por adulto (o preço varia de acordo com o tamanho do grupo)