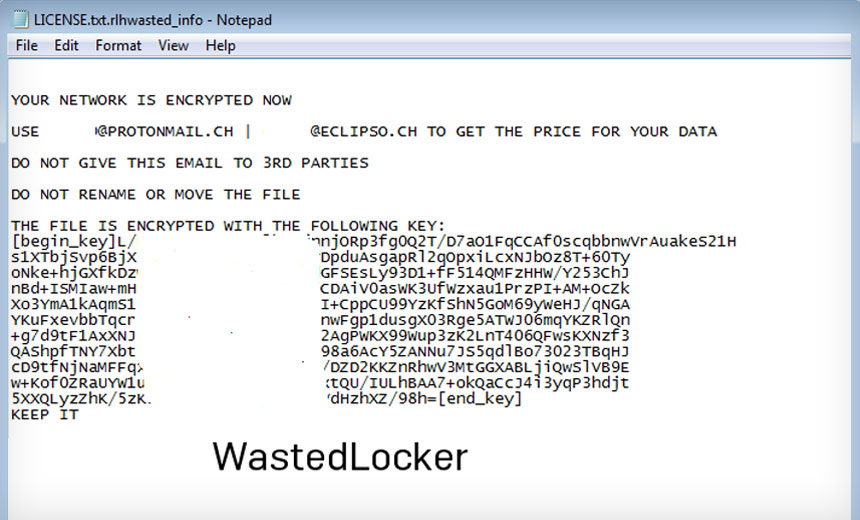
Evolution of the LockBit Ransomware operation relies on new techniques
Descrição
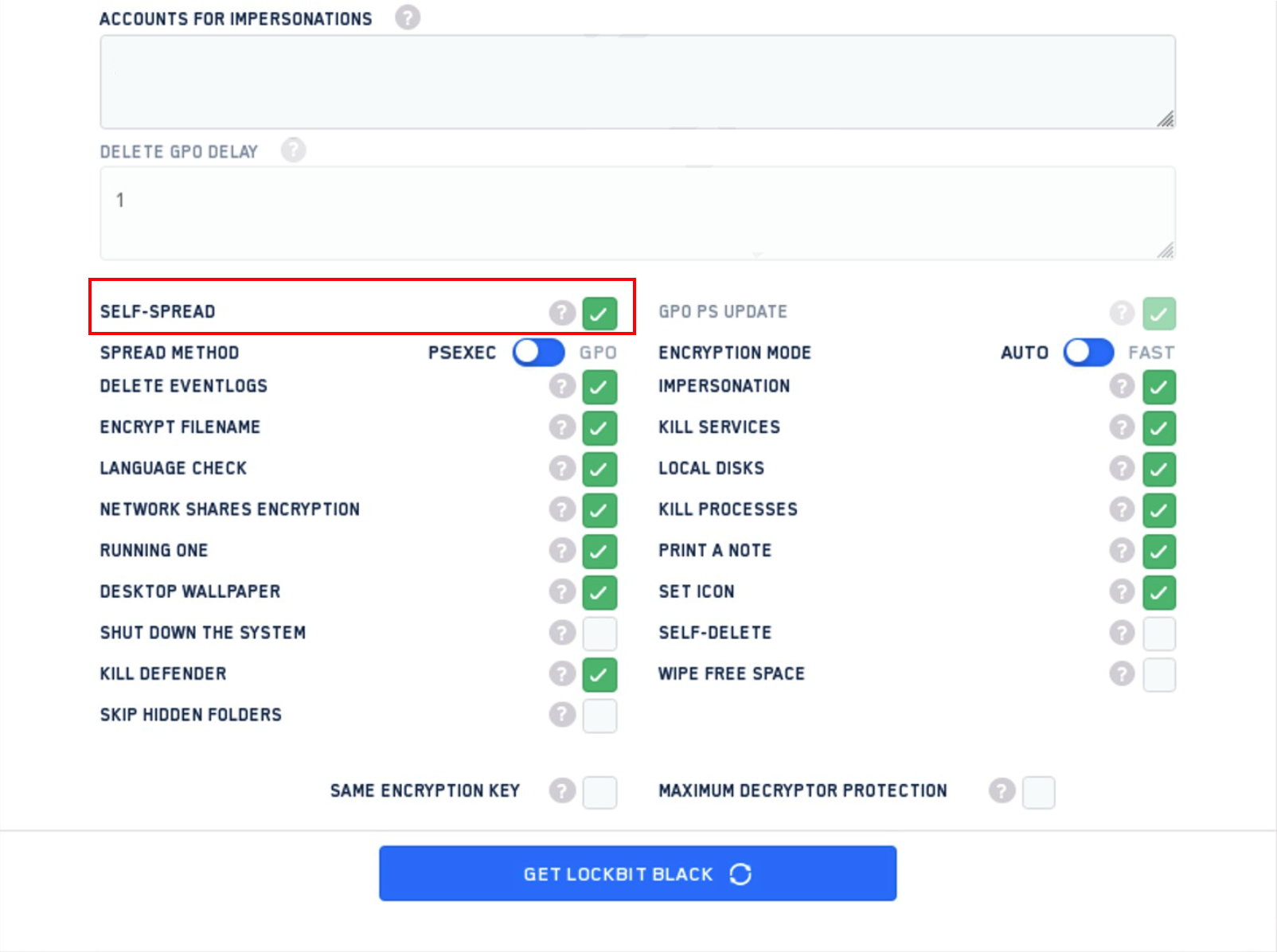
Experts documented the evolution of the LockBit ransomware that leverages multiple techniques to infect targets and evade detection.
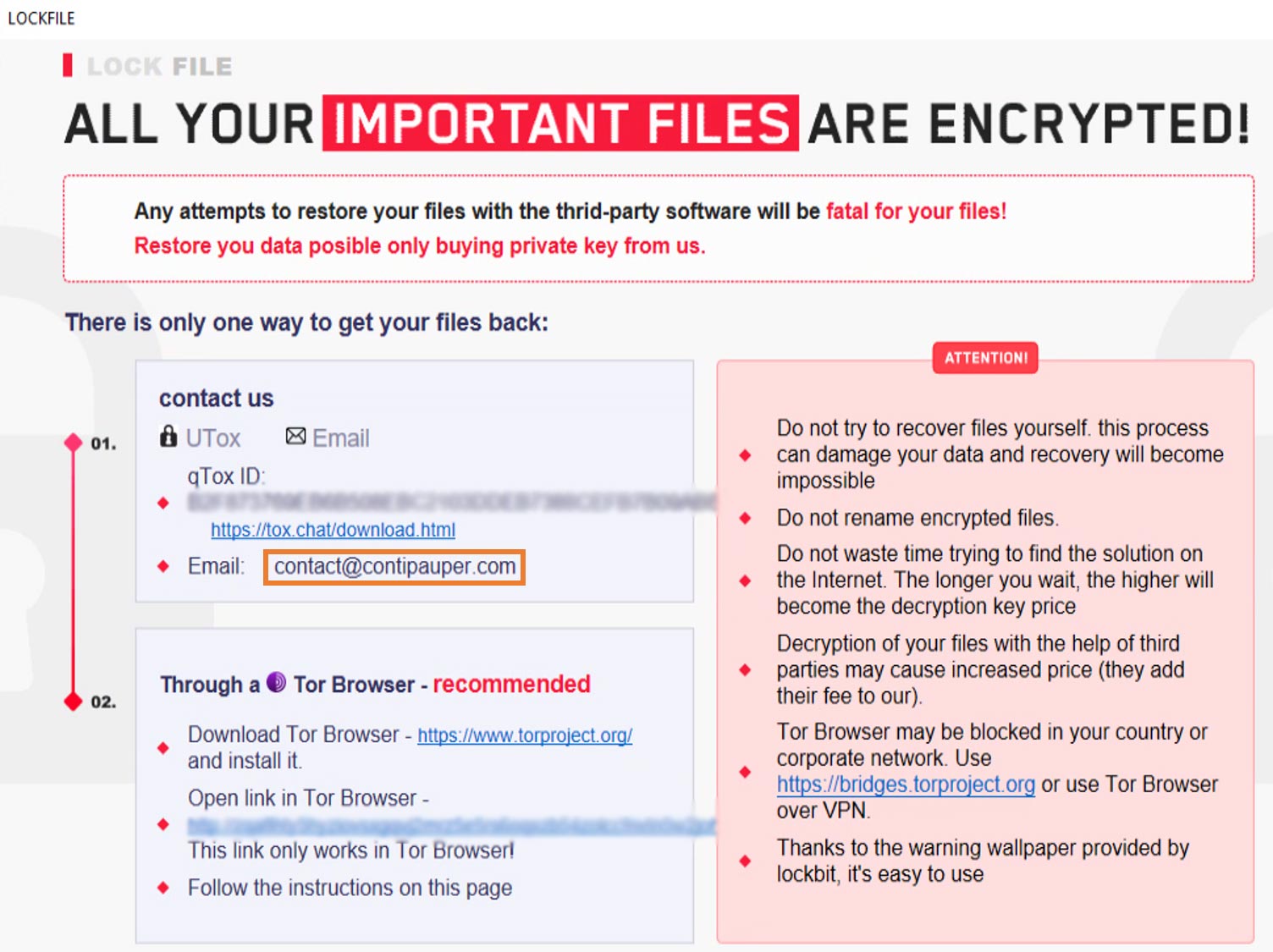
LockBit 2.0 Ransomware Becomes LockFile Ransomware with a Never-Before-Seen Encryption Method

LockBit Ransomware Targets OT

RANSOMWARE TRENDS : H1 2023 Part-2 - CYFIRMA

Evolution of the LockBit Ransomware operation relies on new techniques
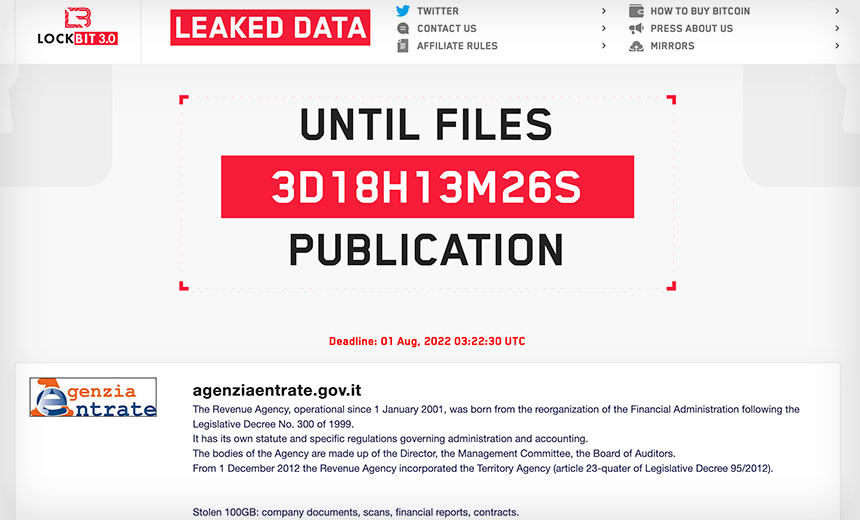
Keys to LockBit's Success: Self-Promotion, Technical Acumen
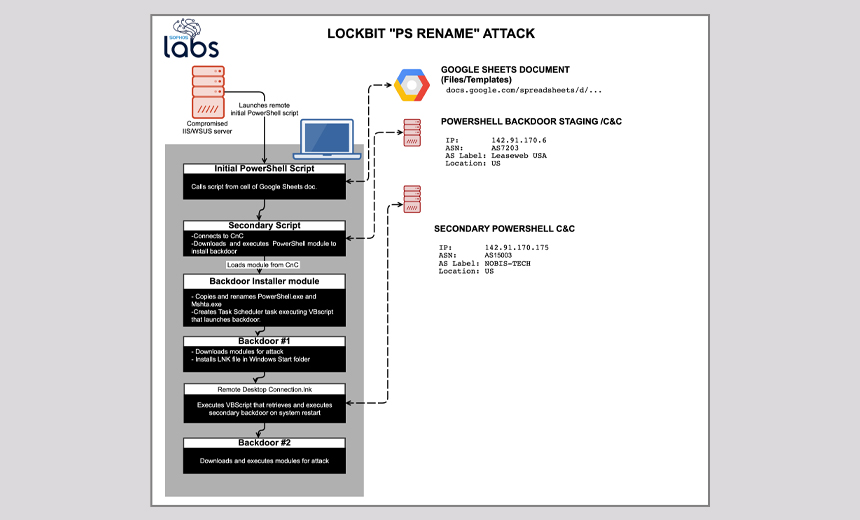
LockBit Ransomware Uses Automation Tools to Pick Targets

LockBit Implements New Technique by Leaking Victim Negotiations

LockBit Ransomware: Battling Cyber Threats - ArmourZero
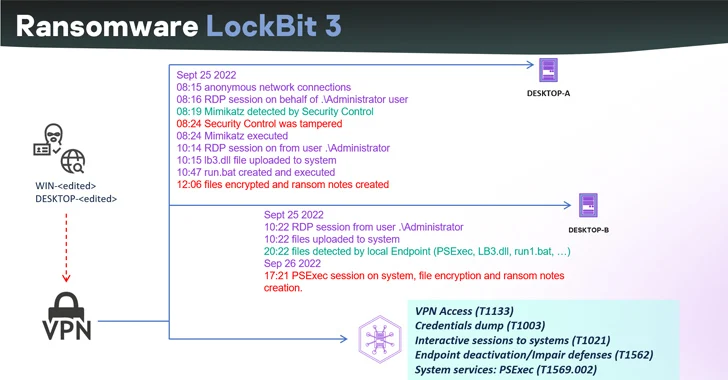
LockBit 3.0 Ransomware Builder Leak Gives Rise to Hundreds of New Variants
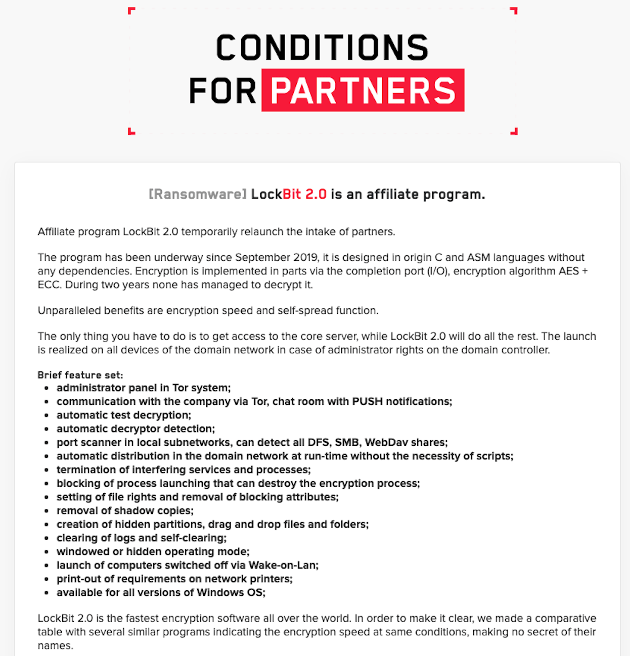
Ransomware Diaries: Volume 1

Ransomware in Operational Technology Environments - SEQRED
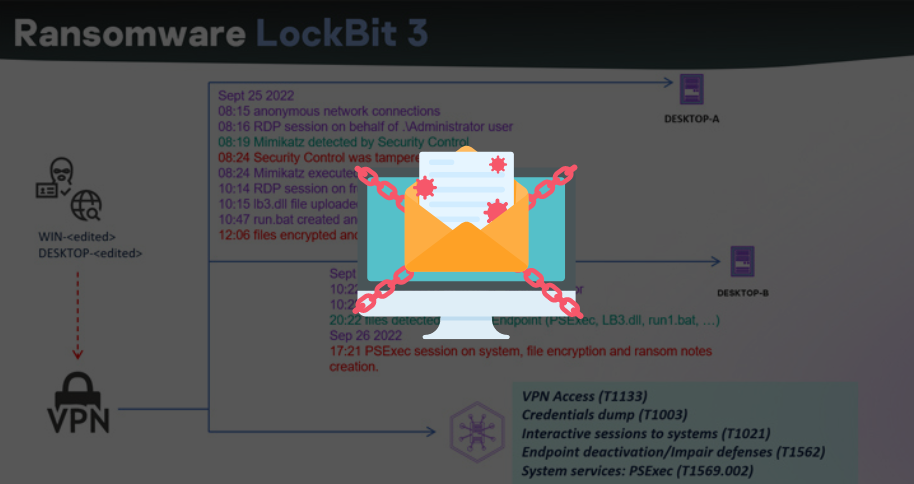
Explosion of New Variants Triggered by LockBit 3.0 Ransomware Builder Leak
Kaspersky crimeware report: ransomware propagation and driver abuse

LockBit 3.0 Ransomware Attack Detection: CISA, FBI, and International Cyber Authorities Warn Defenders of CVE 2023-4966 Citrix Bleed Vulnerability Exploitation - SOC Prime
de
por adulto (o preço varia de acordo com o tamanho do grupo)