Hackers Using New Obfuscation Mechanisms to Evade Detection
Descrição
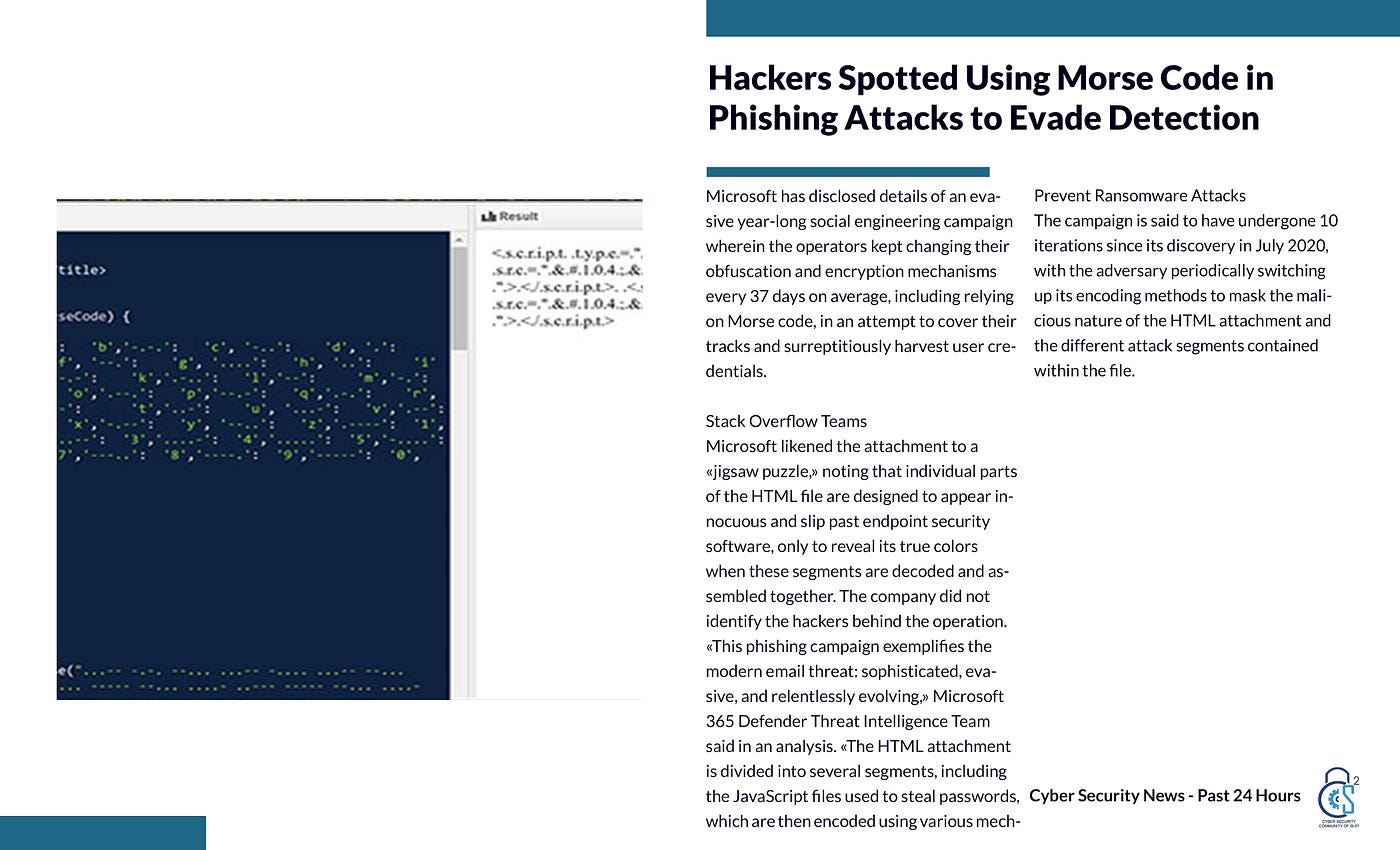
Recently, Microsoft has unveiled details of a deceptive social engineering campaign, in which the operators proceeded to change their obfuscation

Cyble Detects STRRAT Version 1.6 Using Dual String Obfuscation
Guide: Large Language Models (LLMs)-Generated Fraud, Malware, and

Code obfuscation - Cybersecurity ASEE
Hackers Use 'URL Obfuscation' Technique to Deliver Malware

4 Ways Hackers Bypass Fingerprint and Reputation Defense

Using Entropy to Identify Obfuscated Malicious Code

A Look At Some Real-World Obfuscation Techniques

Several Android Malware Apps Use Secret APK Compression to Avoid
Cyber Security News — Past 24 hours, 13.08.2021

BlueNoroff Hackers Utilize ObjCShellz Malware to Create Backdoors

Cybersecurity threats – Can we predict them?

Gamaredon Hacking Group Distribute Malware via Instant Messaging Apps

How hackers are using Google ads network to steal users' data

This Obfuscation Tool Can Evade Most Security Software: Report
de
por adulto (o preço varia de acordo com o tamanho do grupo)







