Malware analysis Malicious activity
Descrição
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows
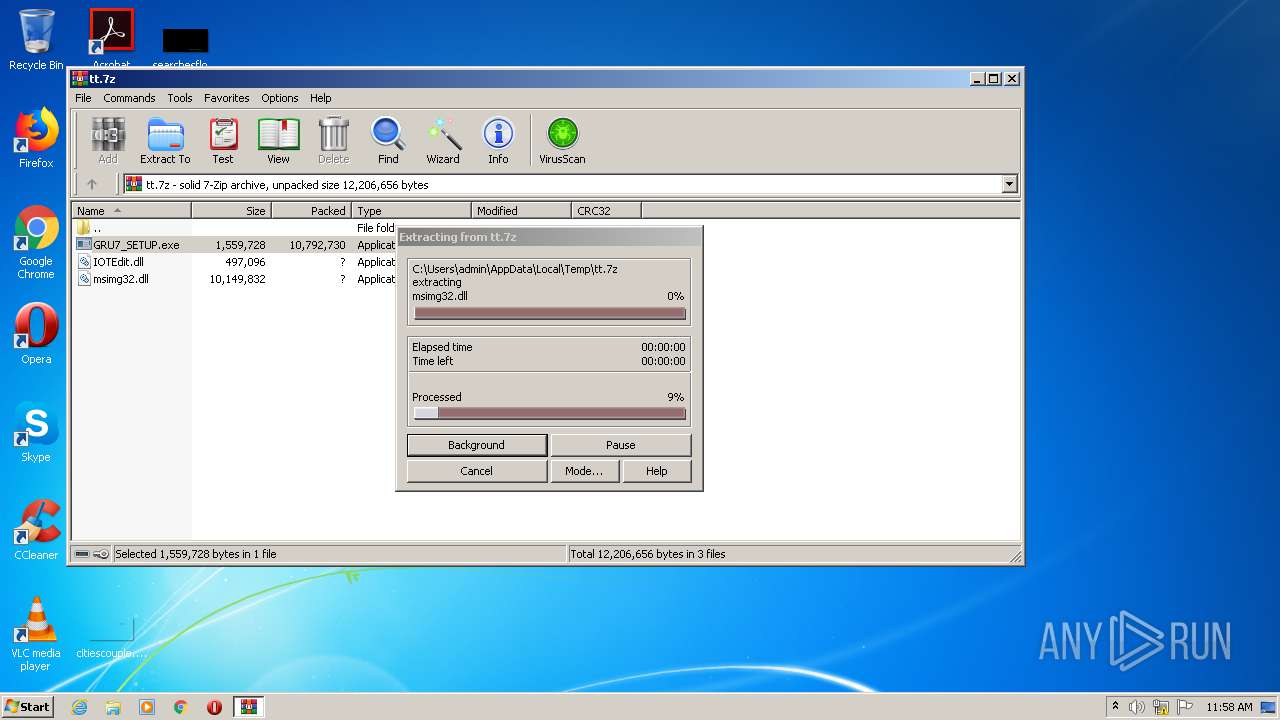
Malware analysis tt.7z Malicious activity

Remediation and Malware Detection Overview

A detailed analysis of the Menorah malware used by APT34

UK and allies support Ukraine calling out Russia's GRU for

StopRansomware: Rhysida Ransomware

Malware Analysis: Protecting Your Network from Cyber Attacks

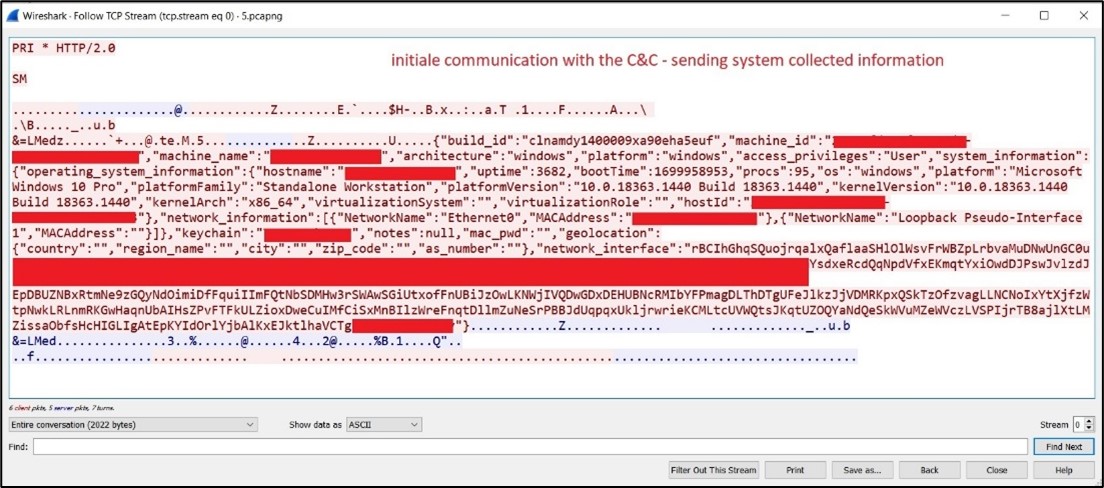
Dynamic malware analysis [34]

Endpoint Detection and Response, Free - What is EDR Security?

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

TryHackMe Hacktivities

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Steps & Examples - CrowdStrike
de
por adulto (o preço varia de acordo com o tamanho do grupo)