Malware analysis Malicious activity
Descrição

Malware Analysis: Steps & Examples - CrowdStrike

What to Include in a Malware Analysis Report

Malware analysis metasploit.bat Malicious activity

Complex 'NKAbuse' Malware Uses Blockchain to Hide on Linux, IoT Machines
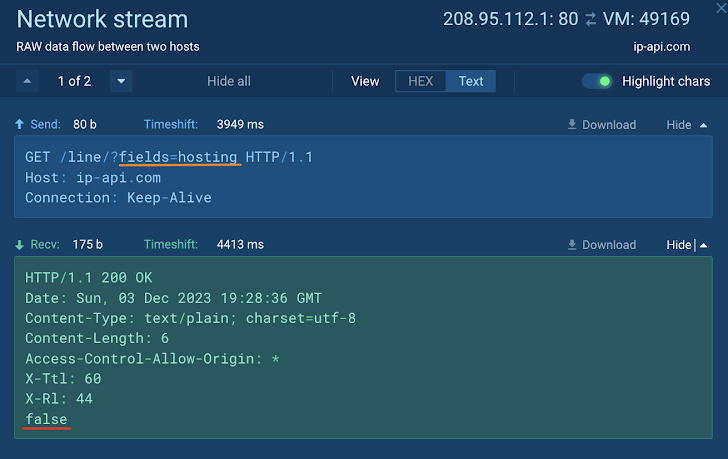
How to Analyze Malware's Network Traffic in A Sandbox

Malware Analysis: Protecting Your Network from Cyber Attacks

Malware analysis index.html Malicious activity

Free Cybersecurity Training and Career Development
MetaDefender Cloud Advanced threat prevention and detection

Interactive Online Malware Sandbox

Malware Analysis: Steps & Examples - CrowdStrike

Info stealers and how to protect against them

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
de
por adulto (o preço varia de acordo com o tamanho do grupo)






