How Do MAC Spoofing Attacks Work?
Descrição
In this blog, we will go into the complexities of MAC spoofing, analyzing its repercussions and emphasizing the importance of having strong security policies in place.
MAC spoofing attack. Download Scientific Diagram

MAC Flooding and Cloning - SY0-601 CompTIA Security+ : 1.4 - Professor Messer IT Certification Training Courses
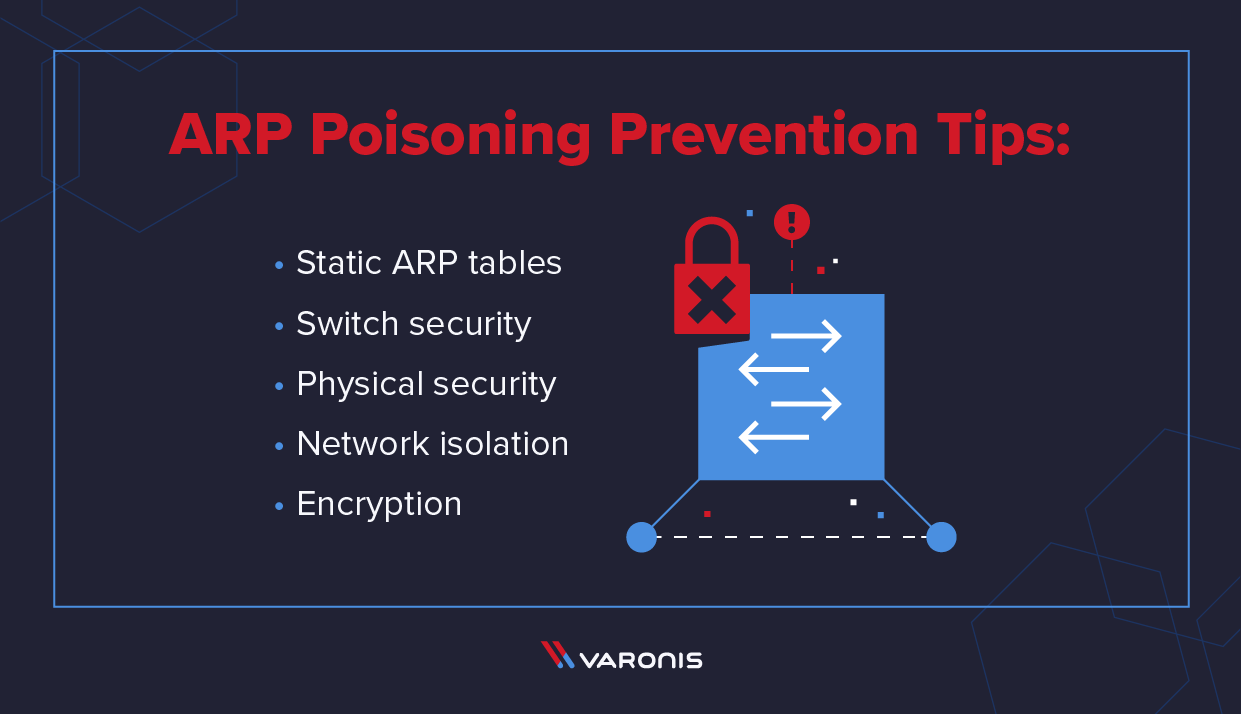
ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks
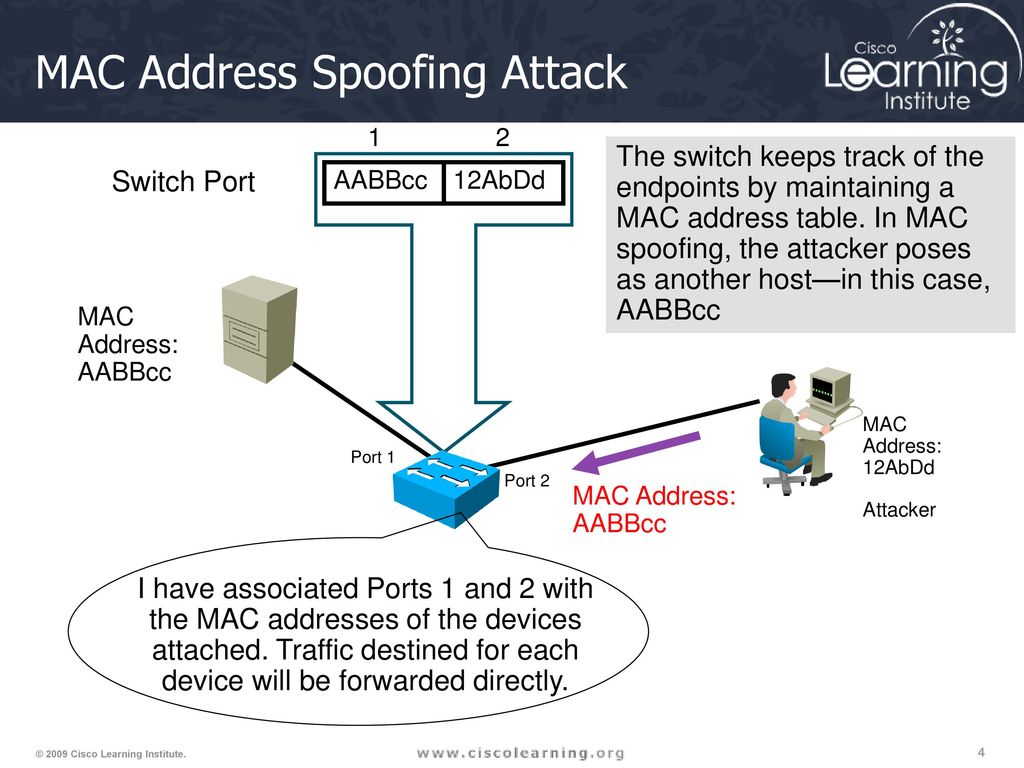
Chapter Six Securing the Local Area Network - ppt download

What is ARP Spoofing? - The Security Buddy
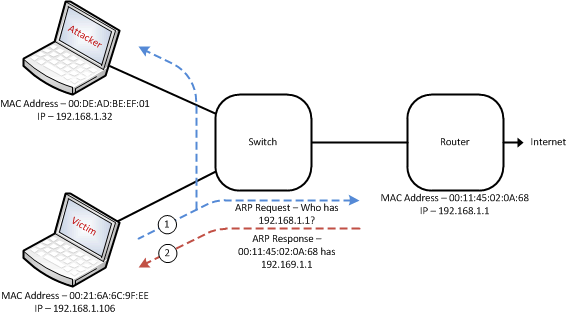
Man in the Middle (MITM) Attacks Explained: ARP Poisoining – ShortestPathFirst
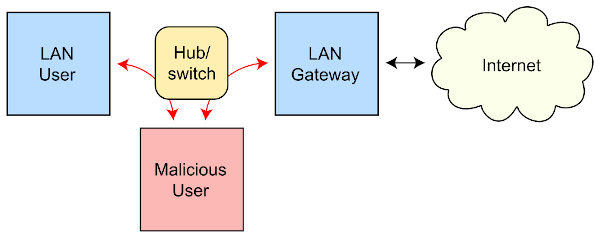
11 Types of Spoofing Attacks You Should Know About
What is a MAC address? How to find it and hide it
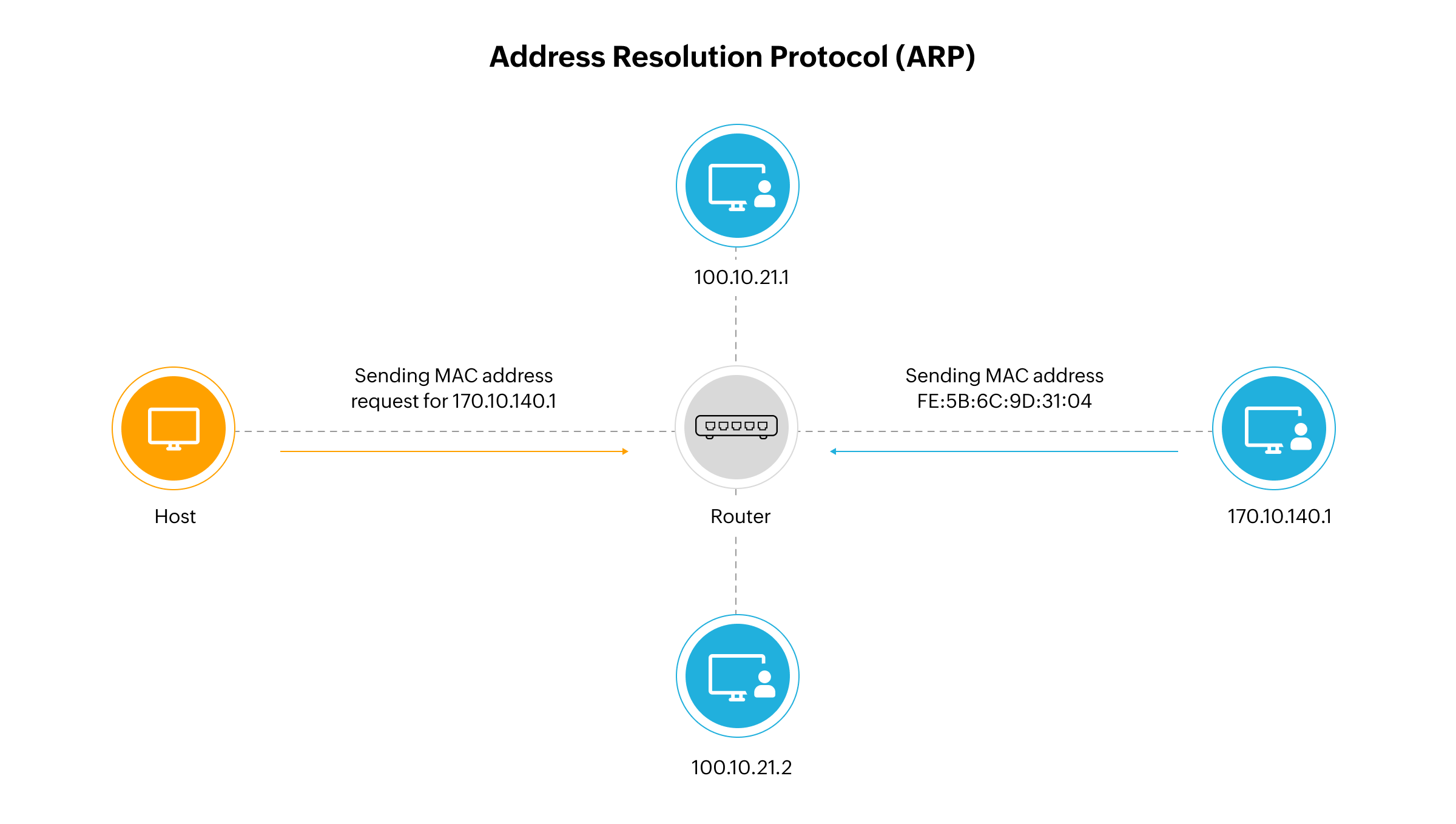
What is Address Resolution Protocol? ARP Solutions - ManageEngine OpUtils

Attacker Spoofing Mac Address
de
por adulto (o preço varia de acordo com o tamanho do grupo)






