Hack Attacks Testing How to Conduct Your - Back to Home
Descrição
Hack Attacks Testing How to Conduct Your - Back to Home

Keeping the gate locked on your IoT devices: Vulnerabilities found on 's Alexa - Check Point Research
List of Data Breaches and Cyber Attacks in 2023 - IT Governance UK Blog
17 Best Penetration Testing Tools For Security Testing
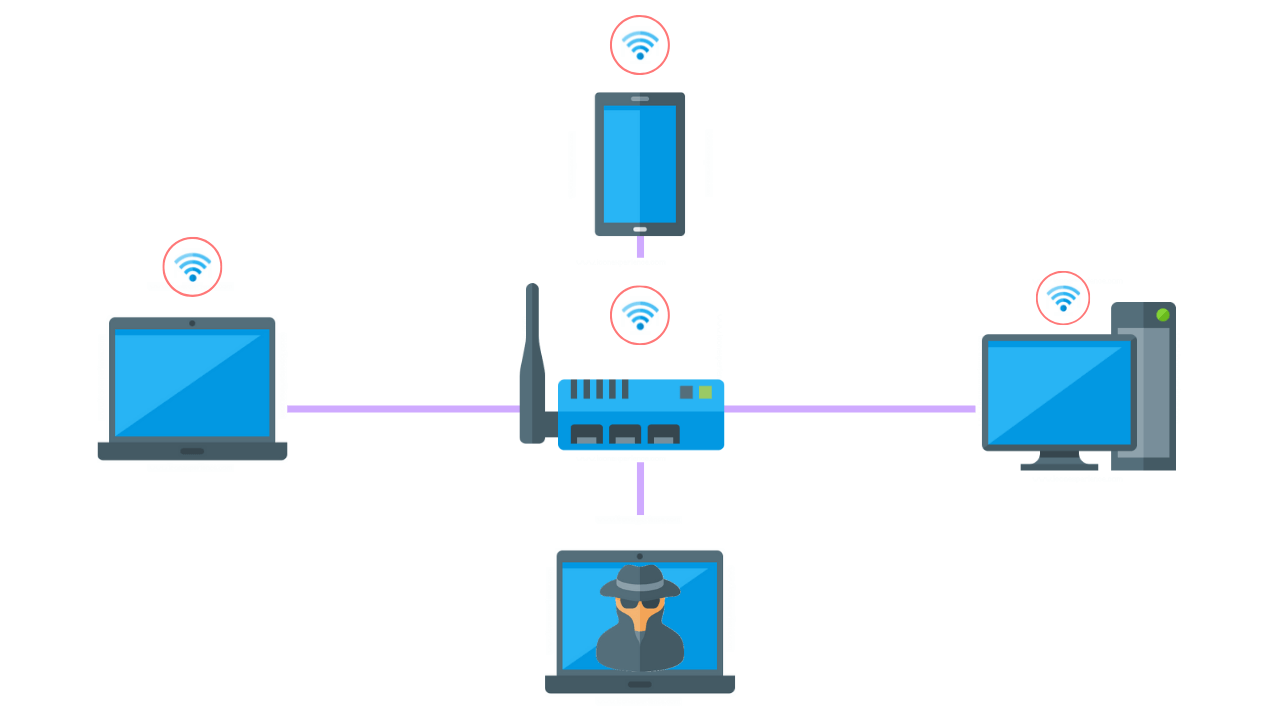
How To Perform A Successful WiFi Penetration Test

How Hackers Outwit All Efforts to Stop Them: It's a Cyber Pandemic.

Hack Attacks Testing: How to Conduct Your Own Security Audit: Computer Science Books @
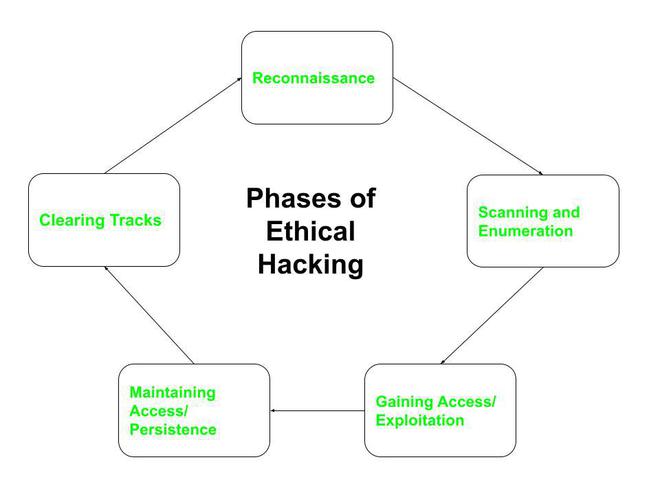
5 Phases of Hacking - GeeksforGeeks

Cybersecurity
JavaScript for Hacking Made Easy: The Expert Guide on Security
What is Penetration Testing and How Does It Work?
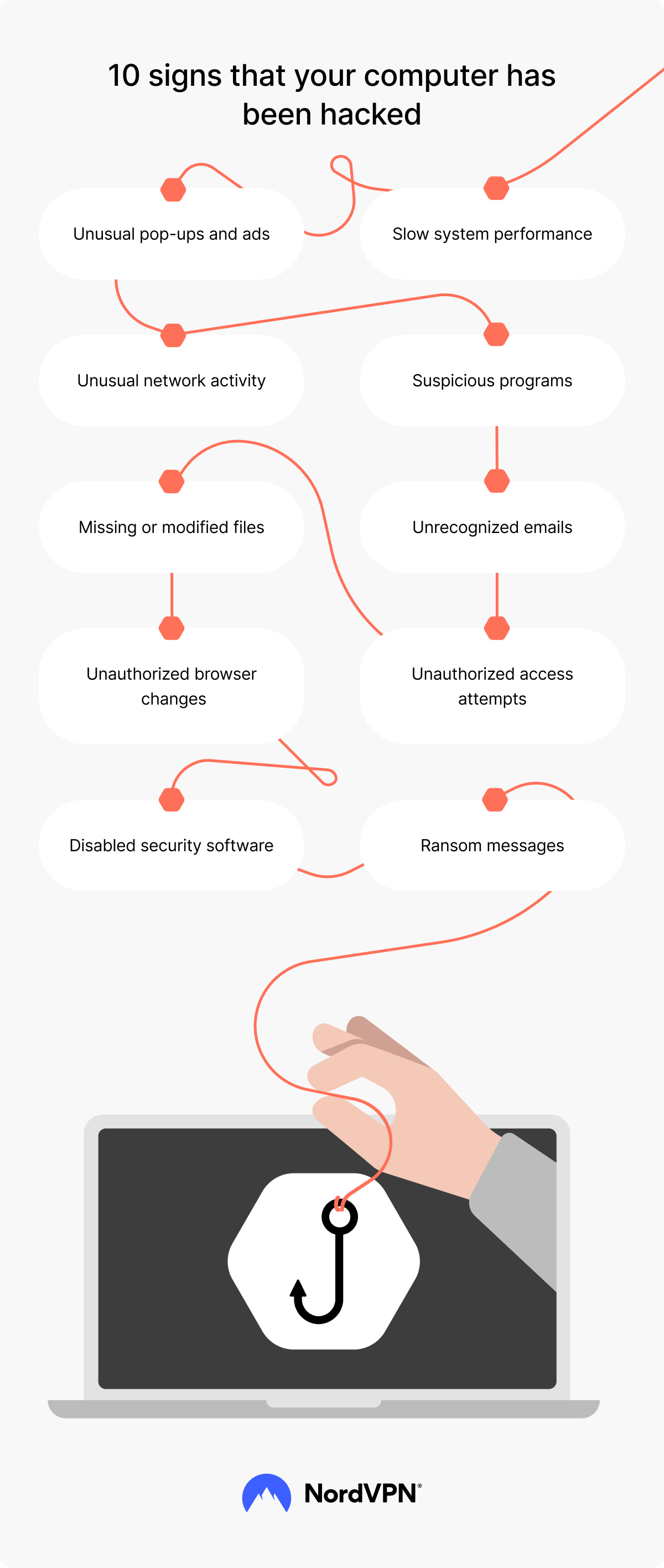
How to tell if your computer has been hacked
de
por adulto (o preço varia de acordo com o tamanho do grupo)




/cdn.vox-cdn.com/uploads/chorus_asset/file/9567289/chrome_2017_10_30_12_15_49.png)