Hackers Target Gamers With Microsoft-Signed Rootkit
Descrição
Kernel mode driver can download second-stage payload directly to memory, allowing threat actors to evade endpoint detection and response tools.

Microsoft Warns of the StrRAT Malware Campaign Targeting Windows

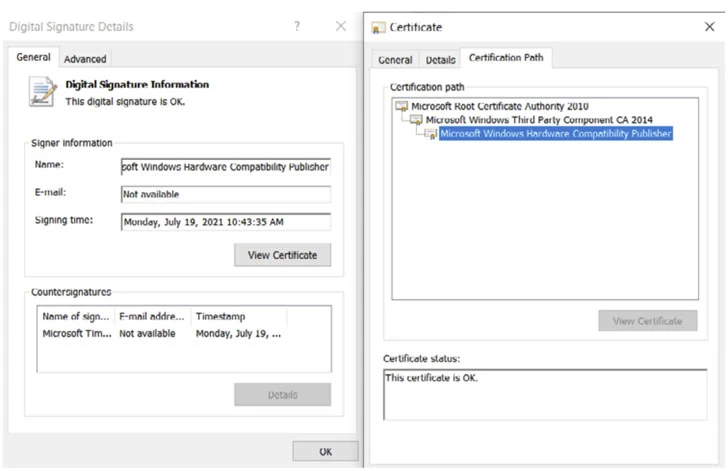
Hackers Trick Microsoft Into Signing Netfilter Driver Loaded With
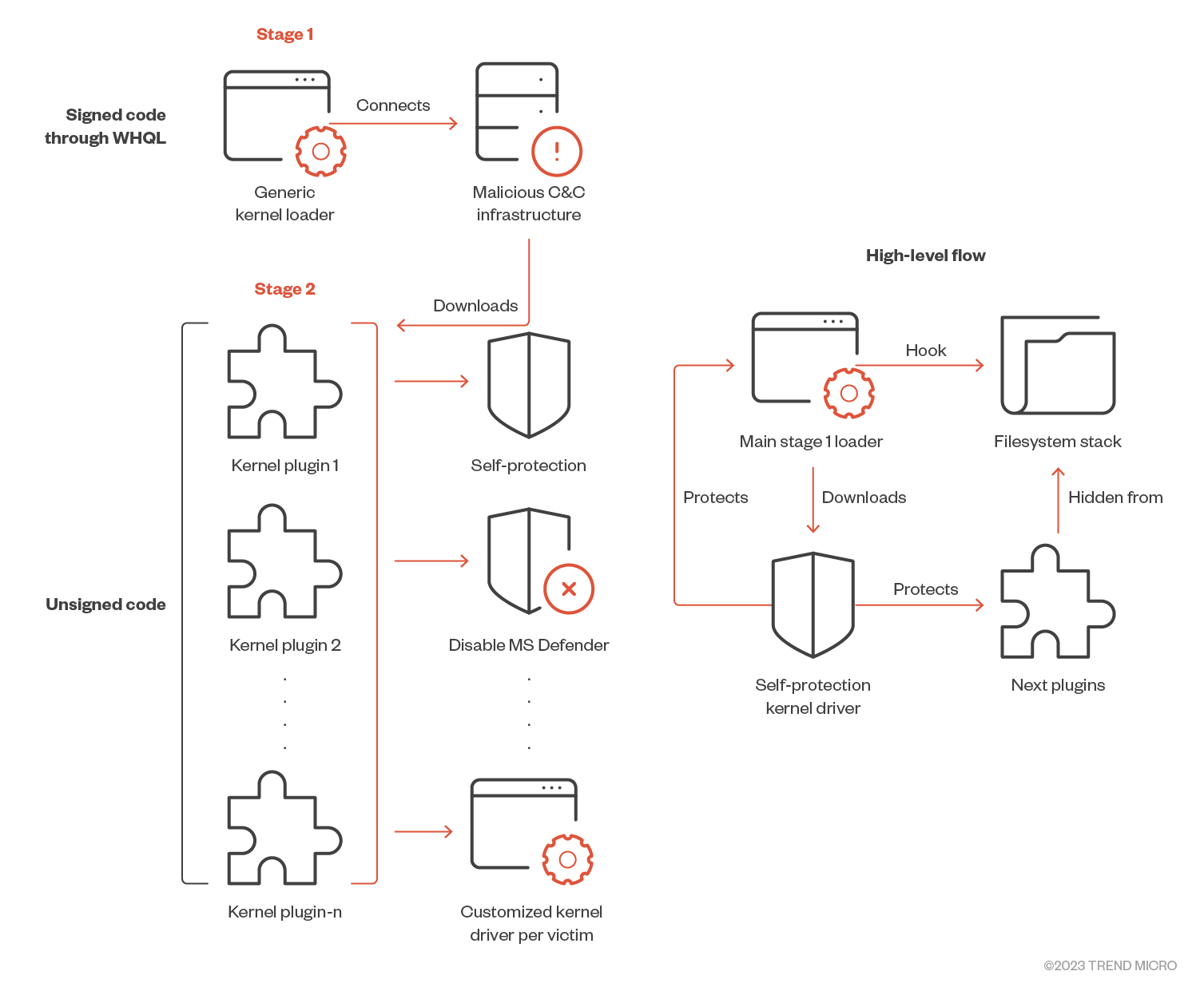
Hunting for A New Stealthy Universal Rootkit Loader

How to Protect Against Rootkit Malware Kernel-Level Attacks

Microsoft signed driver called Netfilter, turns out it contained
Researchers Discover Microsoft-Signed FiveSys Rootkit in the Wild
Microsoft admits to signing rootkit malware in supply-chain fiasco

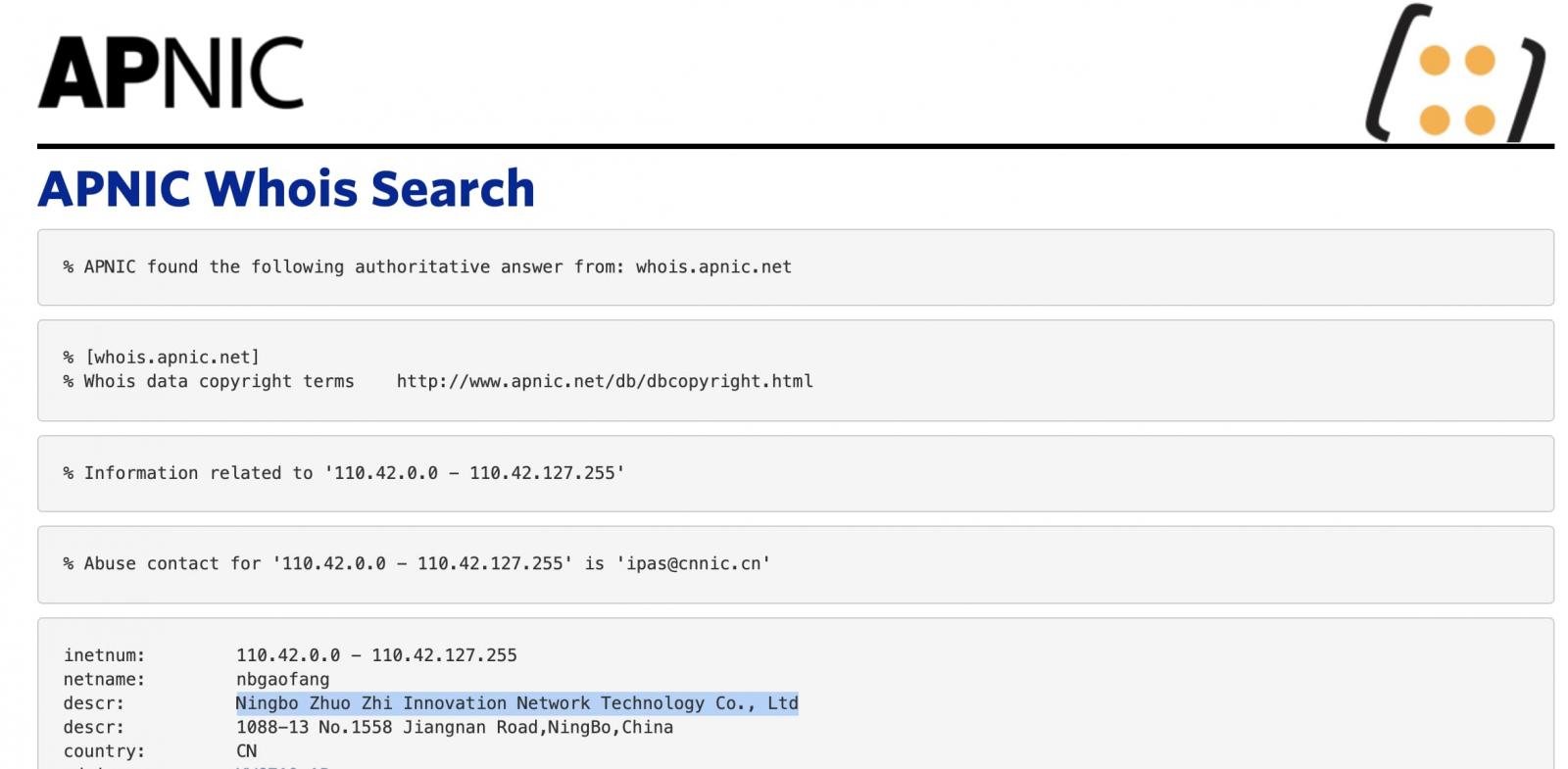
Sam K. on LinkedIn: Chinese Hackers Deploy Microsoft-Signed
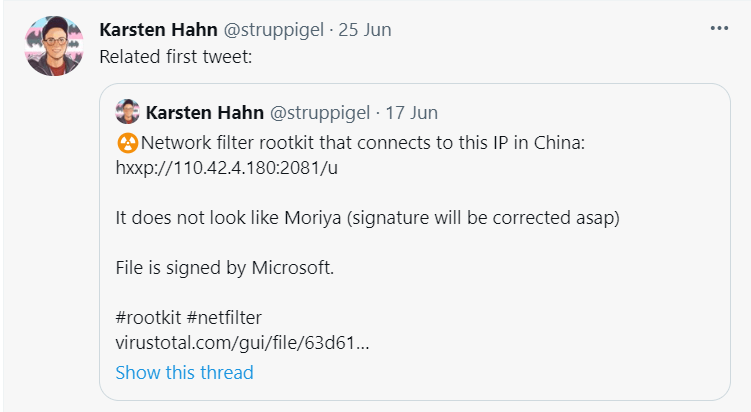
Netfilter Rootkit Malware Targets the Gaming Community: Microsoft

Cisco Talos Reports Windows Policy Loophole Exploited by Threat Actor
de
por adulto (o preço varia de acordo com o tamanho do grupo)