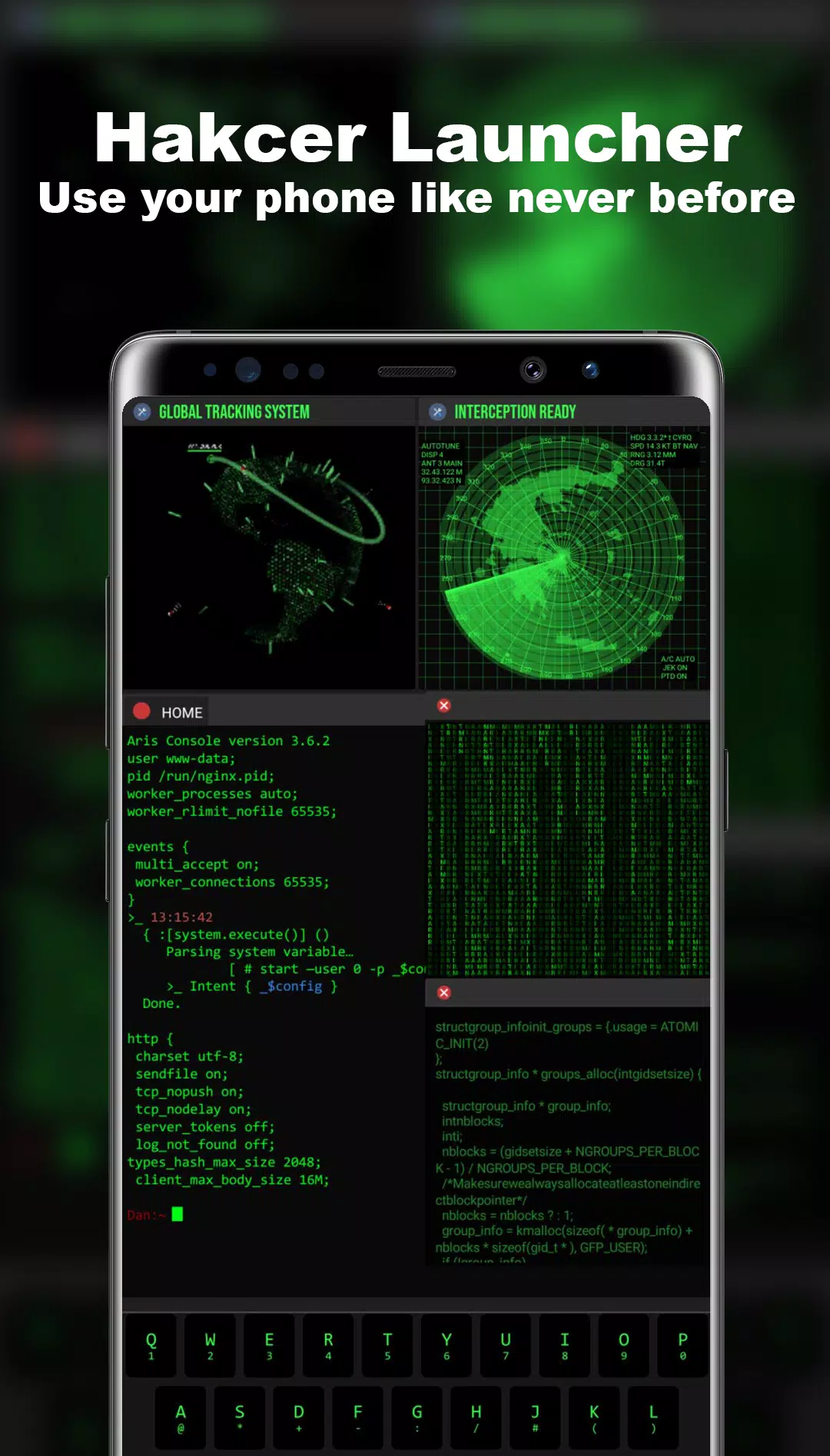
Bluejacking vs Bluesnarfing: Exploring Bluetooth Hacking Variations.
Descrição
Discover the potential security risks of Bluetooth technology, including various types of attacks like bluejacking, bluesnarfing, bluebugging

How to Bluejack a Bluetooth device 2023

CYBERSECURITY
Can you get hacked through Bluetooth? - Quora

PDF) Origin of Bluejacking: Abstract

How to Target Bluetooth Devices with Bettercap « Null Byte :: WonderHowTo

Security threats in Bluetooth technology - ScienceDirect

Bluejacking

THE BLUEJACKING

Module 7: Bluejacking
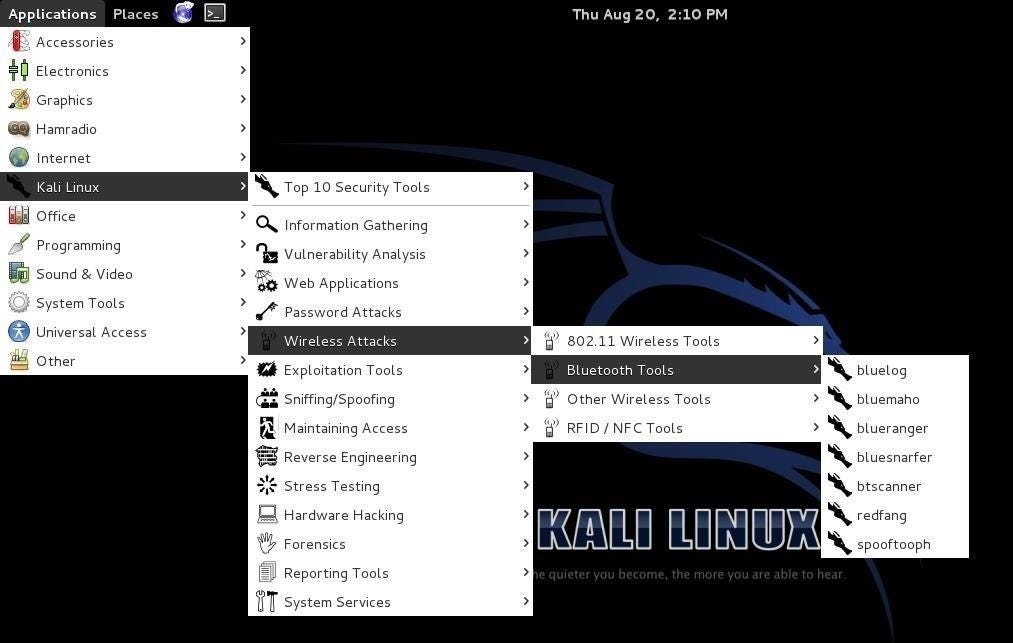
Exploiting Bluetooth driven devices — Bhargav.R, by Bhargav Ravinuthala

Warchalking in Wireless Networks - GeeksforGeeks
de
por adulto (o preço varia de acordo com o tamanho do grupo)