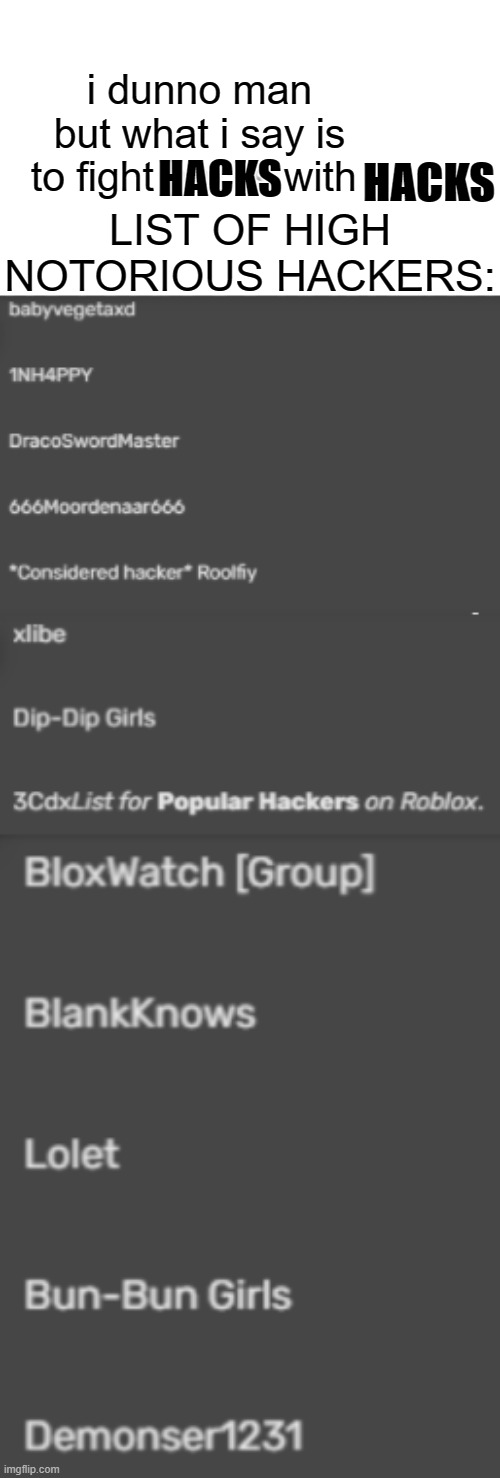
Category:Hackers/Exploiters, Myth Community Wiki
Descrição
Myths who've been accused of/have exploited or hacked in some ways.

Top 6 Most Common Vulnerabilities Found During Penetration Testing

Great Thinkers in Western Philosophy, by Michael Sidiropoulos

News archive

Random Oracle – Building and breaking systems

Hacker Interviews – BannedOffLine, the Admin Of #GhostSquadHackers
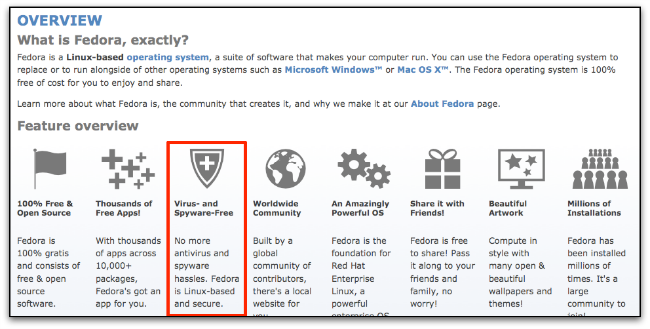
Don't believe these four myths about Linux security – Sophos News

Follow the money! Small donors, big donors, and the midterms

Working For Elon Musk

How Russia Used SolarWinds To Hack Microsoft, Intel, Pentagon, Other Networks : NPR

Survey XII: What Is the Future of Ethical AI Design?, Imagining the Internet

Better than free? The end of FAANG. · Devcon Archive: Ethereum Developer Conference

Cyber Security Courses Free

Cybernetics for the Social Sciences in: Cybernetics for the Social Sciences
de
por adulto (o preço varia de acordo com o tamanho do grupo)