Cmd Hijack - a command/argument confusion with path traversal in cmd.exe
Descrição
This one is about an interesting behavior 🤭 I identified in cmd.exe in result of many weeks of intermittent (private time, every now and then) research in pursuit of some new OS Command Injection attack vectors.
So I was mostly trying to:
* find an encoding missmatch between some command check/sanitization code and the rest of the program, allowing to smuggle the ASCII version of the existing command separators in the second byte of a wide char (for a moment I believed I had it in the StripQ

Machine learning from idea to reality: a PowerShell case study, NCC Group Research Blog


An Introduction to Network Security
Exploit Development: Browser Exploitation on Windows - CVE-2019-0567, A Microsoft Edge Type Confusion Vulnerability (Part 3)

Ethical Hacking - Cmd Hijack - a command/argument confusion with path traversal in cmd.exe confusion-with-path-traversal-in-cmd-exe/
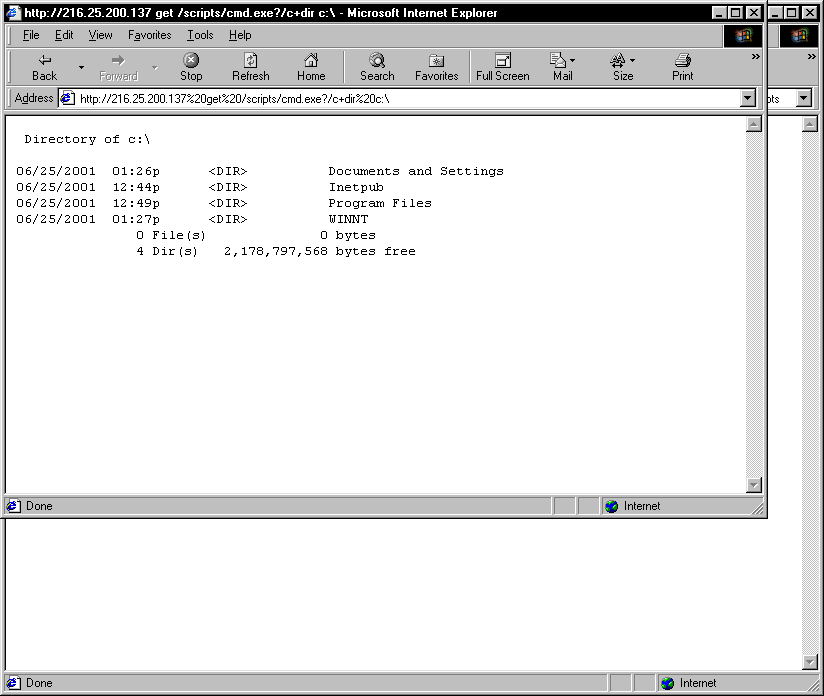
Mad Irish :: IIS Unicode Directory Traversal Exploit Explained

windows - Executing an EXE file using a PowerShell script with arguments for GCDS - Stack Overflow

Curso Metasploit - Part. 2.2 - Comandos de metasploit

JuicyPotato - HackTricks

ExploitWareLabs - Cmd.exe Hijack - a command/argument

PDF) Silent Spring: Prototype Pollution Leads to Remote Code Execution in Node.js
de
por adulto (o preço varia de acordo com o tamanho do grupo)