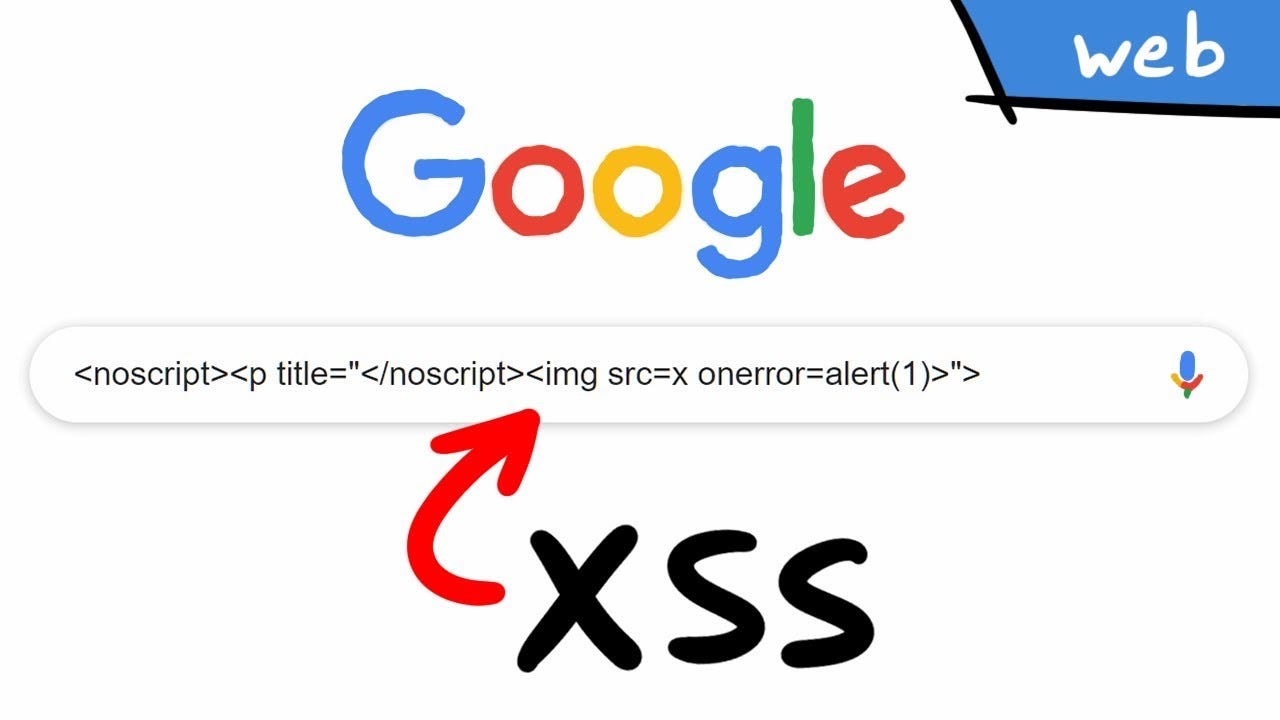
CSP and Bypasses
Descrição
This blog post aims to demonstrate what CSP is and why CSP is implemented. And how attackers can bypass CSP. In this article, I will include how you can bypass some directives to achieve XSS on the target application.

A pen tester's guide to Content Security Policy - Outpost24

Bypassing CSP with JSONP Endpoints - Hurricane Labs
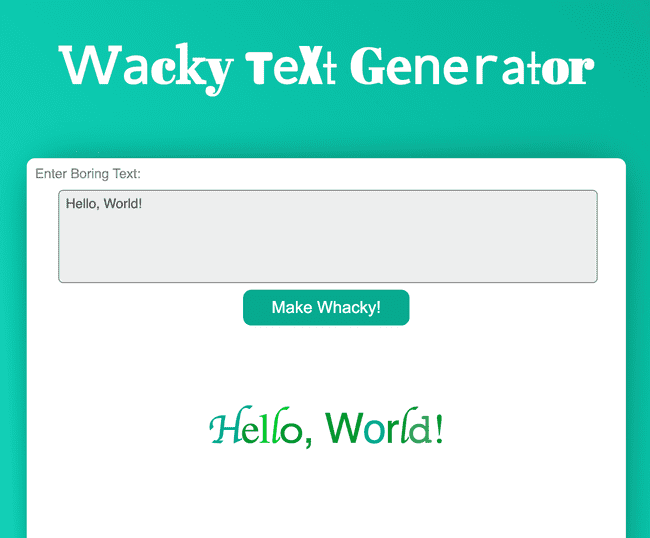
XSS bypassing CSP and using DOM clobbering

Bypassing CSP via ajax.googleapis.com - Center for Cyber Security Training

Using Content Security Policy (CSP) to Secure Web Applications
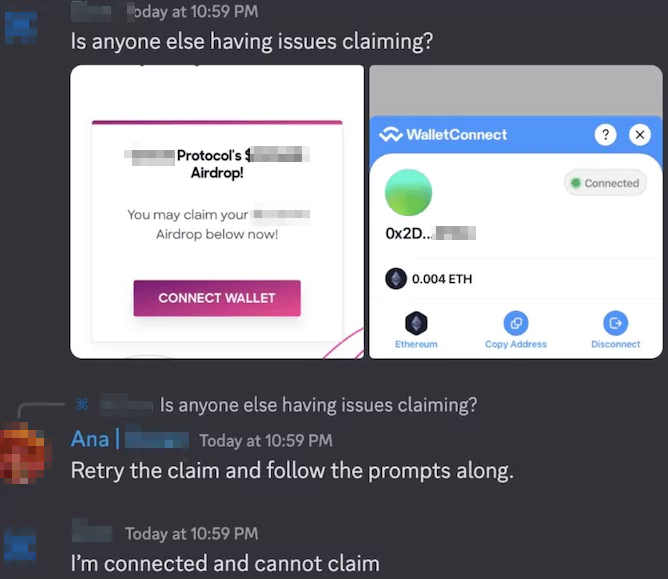
CSP Bypass Unveiled: The Hidden Threat of Bookmarklets
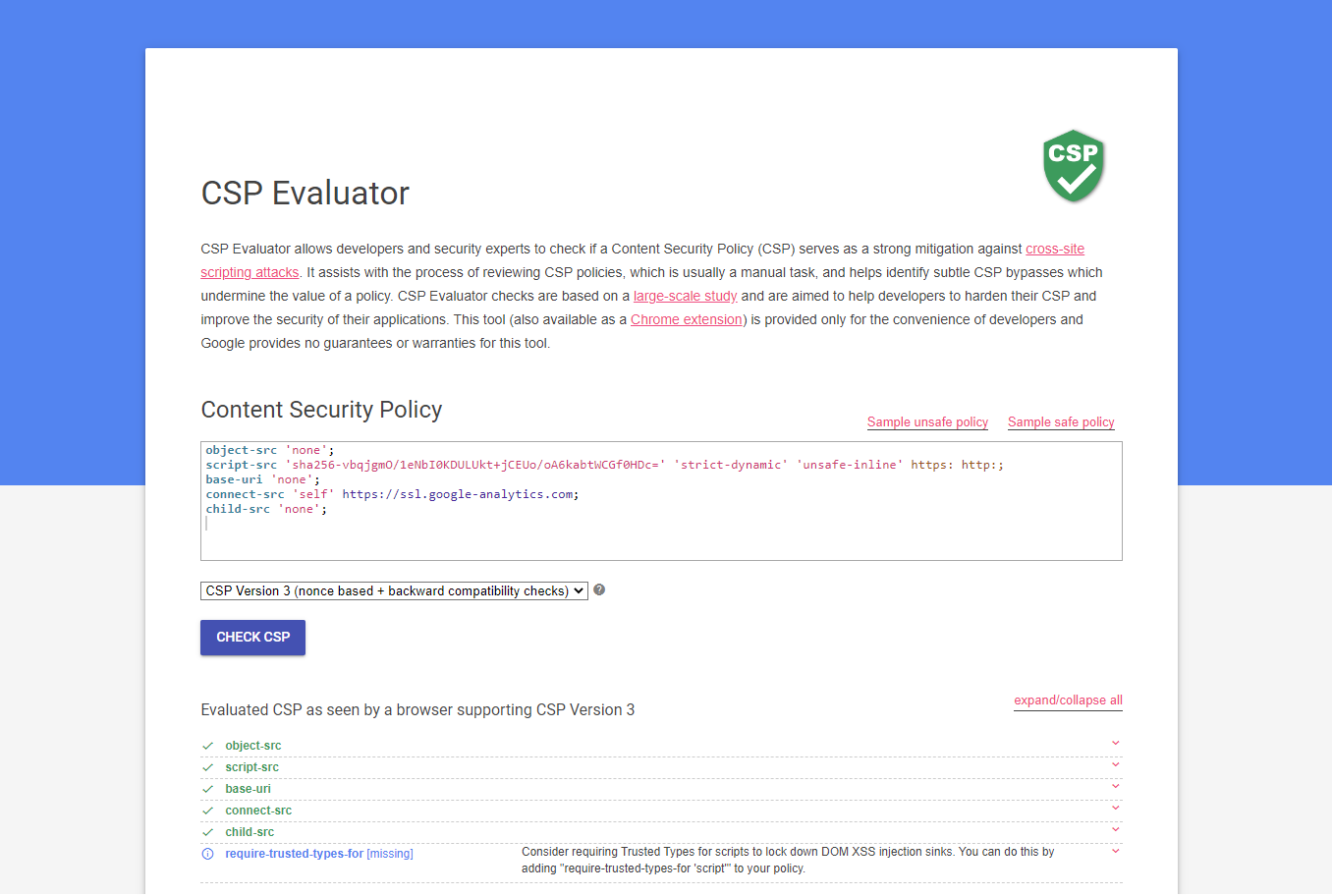
How to use Google's CSP Evaluator to bypass CSP - Web Security Blog

Bypassing CSP with policy injection

Content Security Policy (CSP) and Its Bypasses
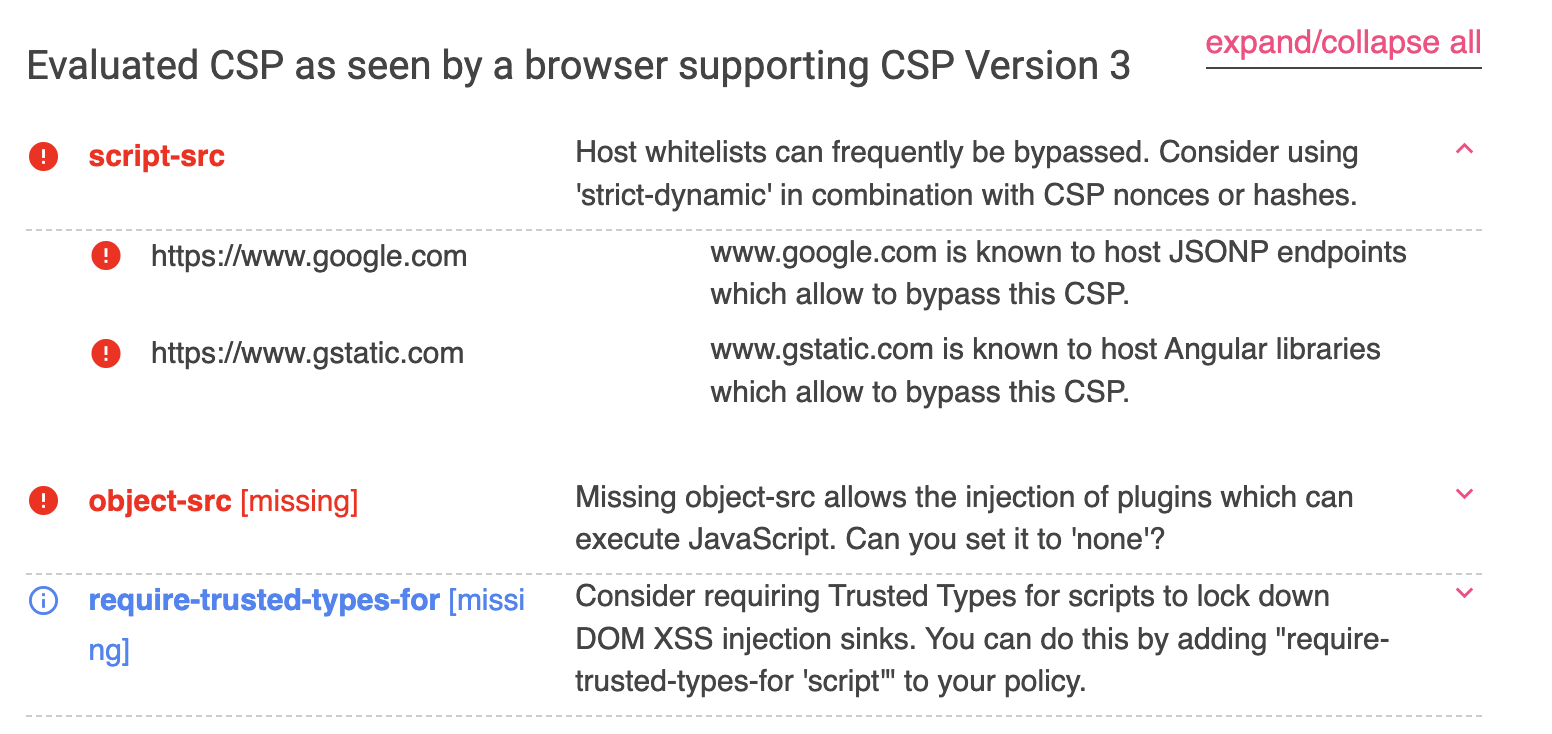
Bypassing Your Defenses: Common CSP Bypasses
de
por adulto (o preço varia de acordo com o tamanho do grupo)