Delay-CJ: A novel cryptojacking covert attack method based on
Descrição
Cryptojacking is a type of resource embezzlement attack, wherein an attacker secretly executes the cryptocurrency mining program in the target host to…

ABC-GSPBFT: PBFT with grouping score mechanism and optimized consensus process for flight operation data-sharing - ScienceDirect

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Circumventing cryptojacking detection by relaying WebSocket requests
CRYINGJACKPOT's general overview

The number of instances of the Coinhive miner scripts found using the
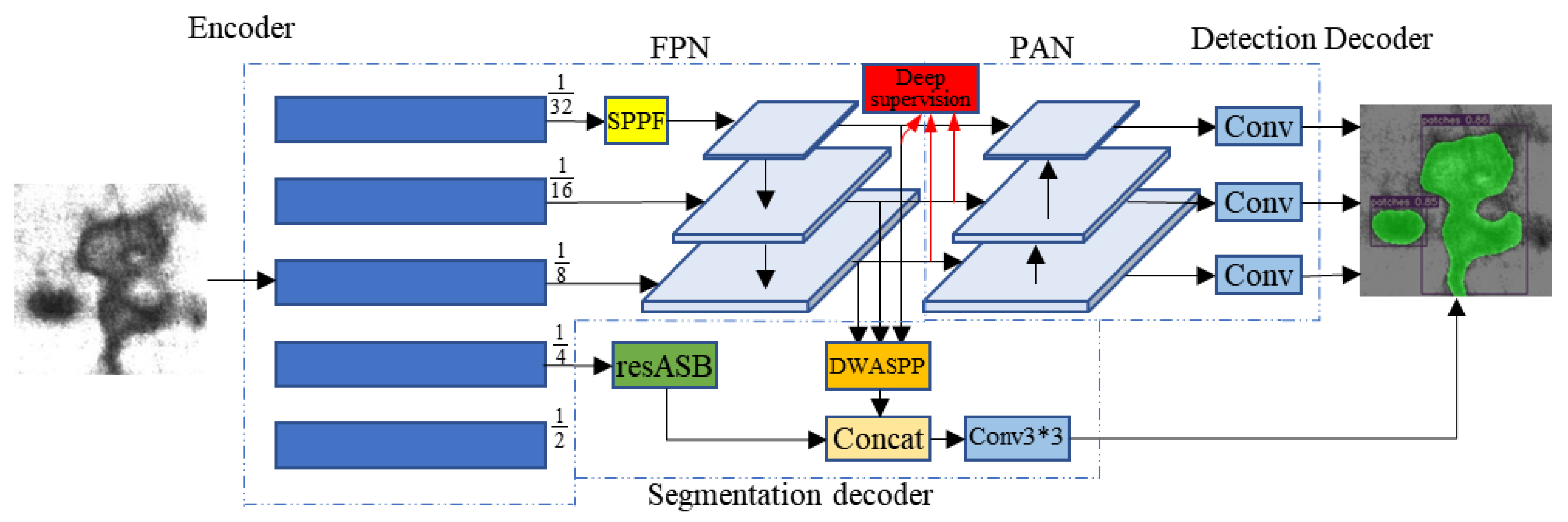
Sensors, Free Full-Text

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

PDF] CoinPolice: Detecting Hidden Cryptojacking Attacks with Neural Networks

Web-based mining scenario. Download Scientific Diagram

Usage of AuthedMine Miner scripts in top one million websites since its

Digital Communications and Networks, Vol 9, Issue 5, Pages 1033-1242 (October 2023)

Top 30 native opcode features that distinguish mining from non-mining
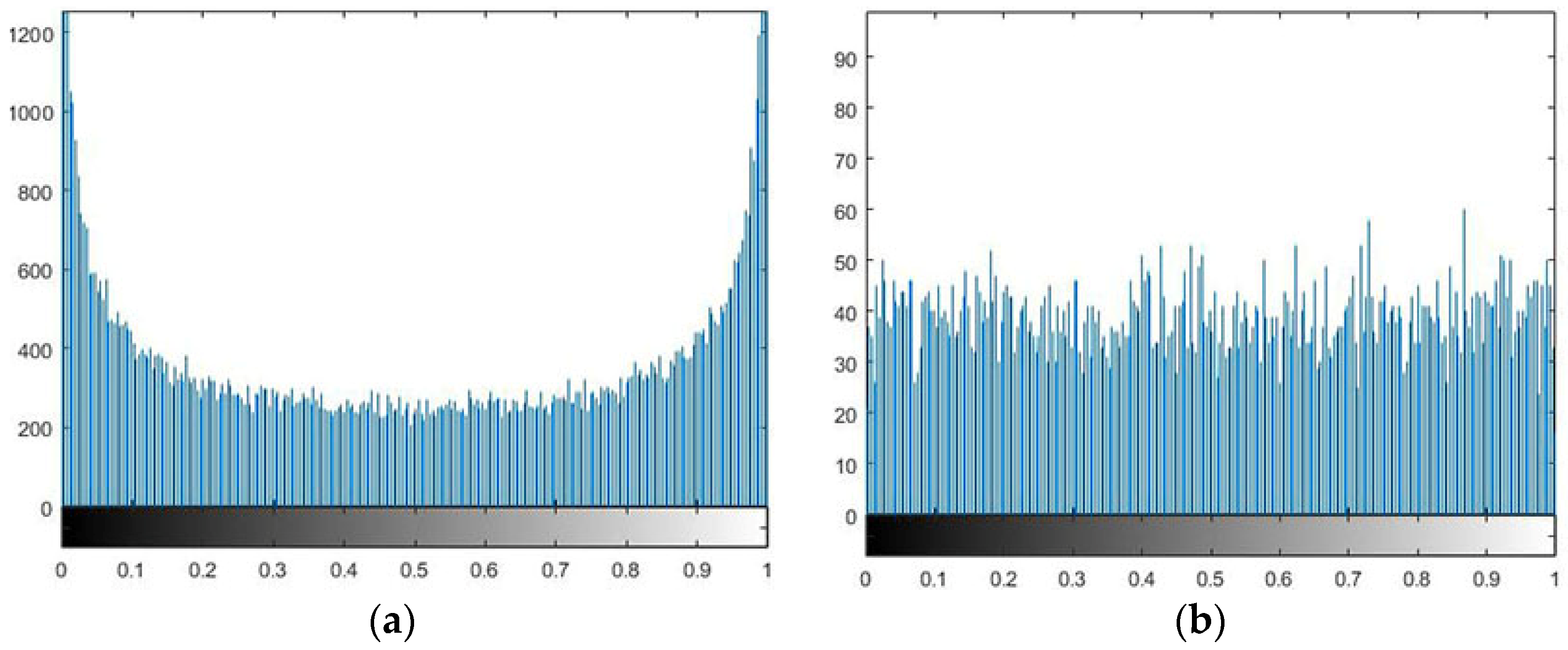
Electronics, Free Full-Text

Full article: Cryptojacking injection: A paradigm shift to cryptocurrency- based web-centric internet attacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)






